Zero added friction for legitimate users. Zero tolerance for compromised credentials.
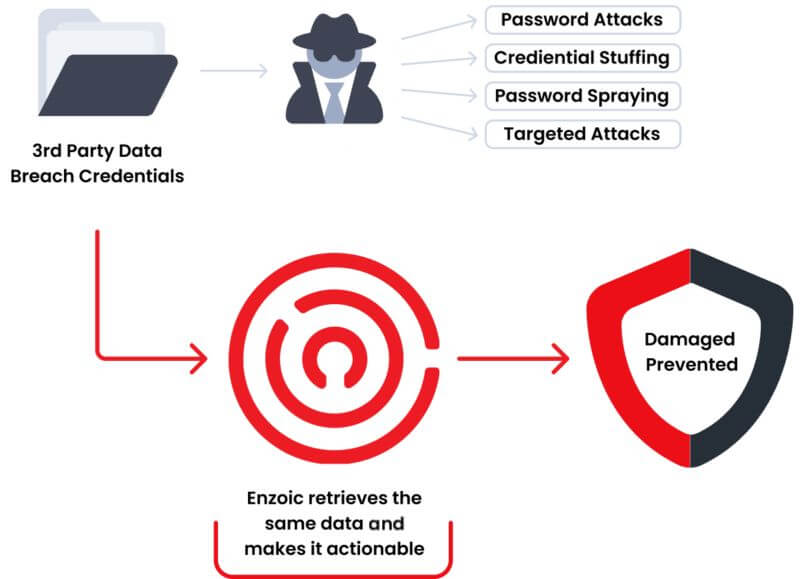
Start for FreeAccount takeover and credential stuffing attacks are growing rapidly as attackers exploit credentials exposed in third-party breaches. With billions of username and password pairs circulating on the dark web and in infostealer malware logs, attackers can hijack accounts at scale using automated tools to exploit reused credentials.
ATO leads to financial losses, additional operational overhead, and brand damage. Studies show the total cost of fraud incidents can be twice the direct fraud amount, and customers often hold the platform responsible—impacting trust, retention, and long-term revenue.
Enzoic enables organizations to screen every login attempt for known compromised credentials and take action in real time to remediate those risks. This level of continuous monitoring—previously available only to large enterprises—helps prevent account takeover without adding friction for legitimate users.
OVERVIEW
Account Takeover (ATO) continues to rise as attackers use credentials exposed in third-party breaches to access customer accounts. With Enzoic, organizations can automatically screen credentials against a continuously updated database of compromised passwords and username/password pairs. This gives you a critical layer of protection against credential-stuffing, brute-force attempts, and automated login attacks.
The credential check runs silently in the background during login, account creation, and password resets. When exposed credentials are identified, your team can trigger immediate remediation—such as forcing a password reset, stepping up authentication, restricting access, or initiating your own custom risk workflow. This allows you to stop attackers without disrupting the user experience.
Although ATO volumes are increasing, the greater challenge is that attackers now use valid—but compromised—credentials sourced from breaches, infostealer malware logs, and the dark web. Traditional authentication only checks whether a password is correct; it cannot determine whether that password has already been exposed and is now high risk. This gap allows attackers to pass legitimate login checks while using credentials that were stolen elsewhere.
A more effective defense requires early detection of compromised credentials. Continuous monitoring helps organizations identify credential exposure as soon as it occurs, reducing the window of opportunity for attackers and enabling faster intervention across login, account creation, and password reset events.
HOW IT WORKS
Traditional authentication only verifies whether a username and password match. It does not reveal whether those credentials have been exposed in a breach or actively circulated among cybercriminals.
Enzoic adds an essential exposure-based check:
This gives IT teams consistent, automated control over credential-based threats while maintaining a fast, seamless login experience for legitimate users.
Organizations gain a reliable, automated control that strengthens authentication without increasing user burden or operational overhead. Enzoic provides a comprehensive set of capabilities designed to reduce ATO risk, including:
Real time detection of compromised passwords and username/password pairs
Continuous database updates sourced from breaches, dark web data, and infostealer logs
Inline screening during login, account creation, and password resets
Flexible remediation workflows aligned to your fraud or risk model
Low-latency API responses for high-volume applications
Zero added friction for legitimate users
Easy deployment through REST APIs and SDKs
Scalable performance for web, mobile, and application environments
Credential exposure is not static. New breaches, infostealer-driven compromises, and data leaks occur daily. Enzoic maintains a database containing multiple billions of compromised credentials, continually expanded through automated collection methods and dedicated threat analyst review.
This gives security and fraud teams ongoing visibility into newly exposed credentials, allowing them to detect risk the moment it appears rather than weeks or months later.
Enzoic uses a privacy-preserving partial-hash comparison method so passwords or full hashes never leave your environment. Additional safeguards include:
This architecture delivers strong ATO protection without exposing sensitive data.
Built on AWS and designed for high-traffic environments, Enzoic typically responds in ~200 – 300 milliseconds or less. Organizations can screen every login in real time without adding friction to user workflows.
Most teams integrate Enzoic into their authentication workflows in hours—not weeks. REST APIs and SDKs make it straightforward to add credential exposure checks to login and password-change events. Support is available to help teams design the right implementation based on their authentication architecture.
Resource Hub
Read how to battle account takeover risks. Start cross-checking current credentials without adding friction to the user experience.
Resource Hub
Read this e-Book to discover the four ways to safeguard your organization with a robust password policy.
Blog
All enterprises balance their need for strong authentication security against a frictionless user login process. How some solutions can help that balance.
Enzoic eliminates the risk of allowing compromised credentials to be used in your authentication flow. It provides a simple, cost-effective way to strengthen the password layer and reduce account takeover attempts.
Applications that store financial assets, reward balances, personal information, or service access are common targets, as attackers monetize compromised accounts in multiple ways.
Enzoic maintains a continuously updated database of multiple billions of compromised credentials. Data is sourced through automated collection and validated by our threat analyst team.
Enzoic’s API is hosted on AWS and architected for low-latency global performance. Typical response times are around 200 – 300ms or less.
All credentials in our database are encrypted, salted, and strongly hashed. Enzoic uses a privacy-preserving partial-hash comparison that ensures no clear-text password or full hash leaves your environment. Submitted data is not logged, and memory is cleared immediately after processing.
Pricing scales based on usage volume and services required. Volume discounts are available. Please request a custom price quote today.
Integration is straightforward with simple REST APIs and SDKs. Most teams incorporate API calls into login and password-change workflows. Please see our API docs for details.
Yes, Enzoic offers a free trial so organizations can evaluate the solution in their environment.
Block cybercriminals from using stolen credentials for account takeover attacks and credential stuffing.
Experience Enzoic