Enzoic’s breached credential alerts keep you informed and protected.
Try Now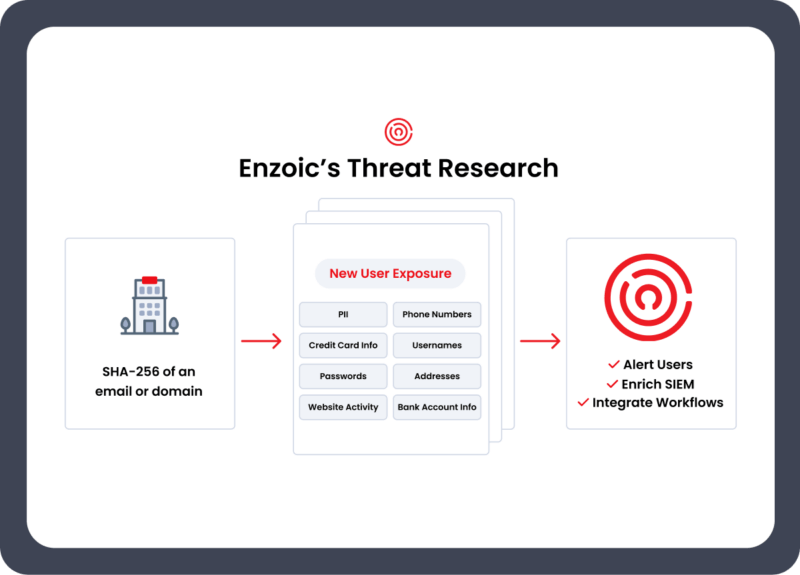
HOW IT WORKS
Our threat researchers continuously scour the public Internet and Dark Web to find stolen credentials and immediately report details on any compromised username and password for your customers, employees, or partners.
HOW IT CAN HELP ME
Avoid password reuse and let Enzoic do the work to provide early detection of data breaches and stolen credential to your organization.
Monitor by domain, individual accounts, or by integrating into your directory.
Receive rich details about the source of the credential or password exposure and the lists of affected users.
Enrich threat intelligence for your SOC and SIEM using our API feed.
FEATURES
Even if your organization has not been breached, password reuse puts it at risk. Protect your data and organization with these key features:
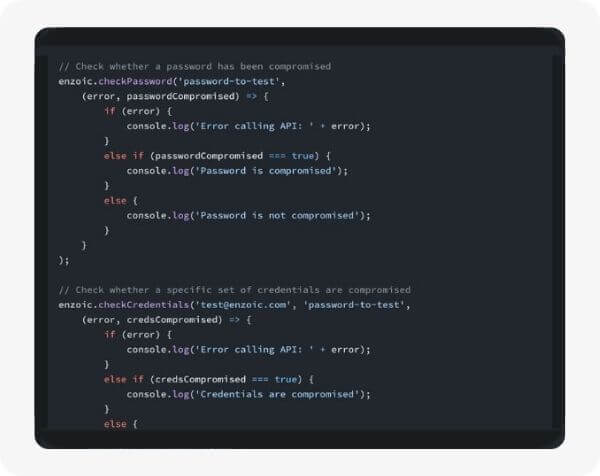
The Breach Monitoring API allows you to register email addresses, usernames, and email domains with Enzoic so you can be notified about future breaches that involve them.
Explore quick-start guides, code snippets, and a comprehensive resource library to integrate into your workflows.
Read DocsPrice
Free
Accounts: 10 Free, then $0.50 each Credentials: 10 Free, then $0.50 each Domains: Contact Us
Contact Us
Billing Cycle
-
Monthly
Custom
Payment Methods
-
Credit Card
Custom
Accounts
10
Unlimited
Custom
Credentials
10
Unlimited
Custom
Domains
-
Unlimited
Custom
Support
Self-Service / Knowledge Base
24-hour response during business week
4-hour response during business week
SLA
-
-
Custom
User Account Monitoring
Domain Monitoring
User Credentials Monitoring
Blog
What are the new domains cybercriminals are exploiting? Read how companies can fortify their defenses in this ever-shifting battleground.
Blog
Infostealers have moved from a ‘consumer vulnerability’ to an organizational one. With a perfect storm of circumstances at hand.
Blog
The average cost of a data breach in 2023 jumped to $4.45 million, marking a 15% increase over the past three years according to IBM's report.
Receive automated exposure alerts when your compromised accounts are leaked.
Try for Free