A dark web monitoring solution that continuously screens for exposed data to protect user identities and digital assets.
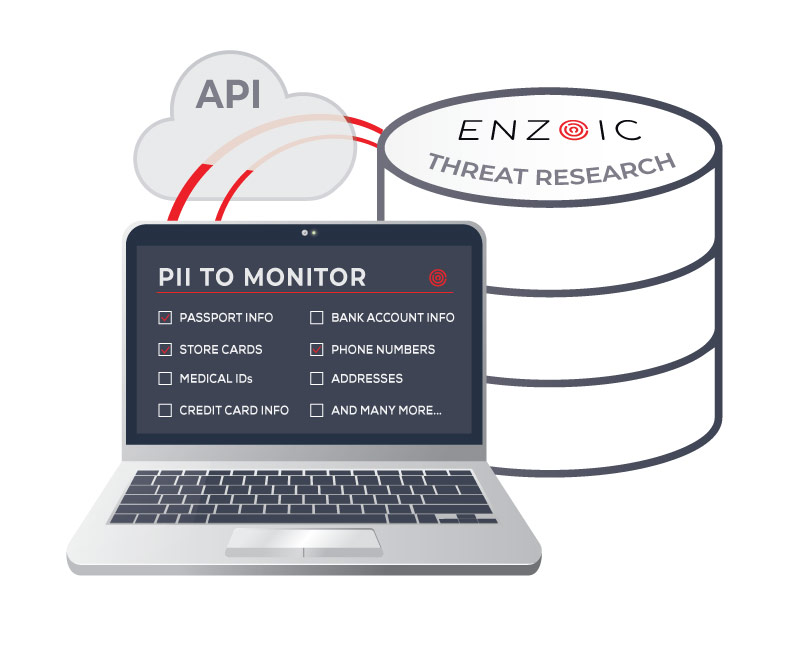
HOW IT WORKS
Enzoic’s Identity Breach and PII Monitoring helps organizations continuously monitor for the exposure of personally identifiable information (PII), reducing the risk of identity theft and data abuse for financial gain, fraud, or account takeover. Our straightforward monitoring service allows organizations to safeguard their users without building complex queries and parsing data.
Download the Identity Breach Monitoring BriefHOW IT CAN HELP ME
Be instantly notified of compromised PII, including credit cards, Social Security Numbers, cryptocurrency wallets, and much more.
Enzoic’s extensive research capabilities provide comprehensive visibility into Dark Web data to protect PII and your users.
Continuously track the PII that’s relevant for your workflows by subscribing to other data elements outside Enzoic’s default PII list.
Enzoic gathers and provides data in real-time, without the delays and resources required for you to periodically query an unstructured database.
Prompt notification allows for swift remediation, enabling users to safeguard their accounts and data from identity theft, fraud, and unauthorized access.
FEATURES
Featuring a user-friendly API that seamlessly integrates and expands with your projects.
Real-time alerting of new exposure, plus optional querying of past breach data where identities were previously compromised.
Enzoic’s dedicated research team and proprietary tools, provide immediate and actionable alerting.
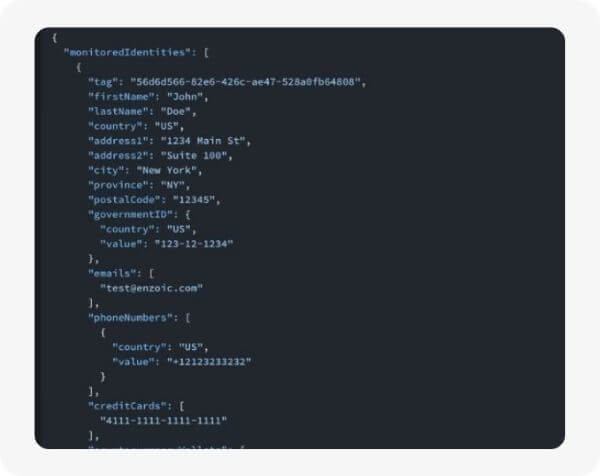
The Identity Breach Monitoring API allows you to register complete identities with Enzoic, so that you can be notified about future breaches that involve them.
Explore quick-start guides, code snippets, and a comprehensive resource library to integrate into your workflows.
Read DocsBlog
Sensitive personal information is highly sought after by cybercriminals. As identity theft incidents continue to rise, organizations need effective solutions to protect PII.
Blog
What is identity theft, and what’s happening to increase the impact so dramatically? Read what enterprises can do to make positive change.
Blog
Digital identities are the keys to our online worlds. Recent analyses uncover why organizations must take a strong approach to security.
Talk to us about integrating Dark Web Monitoring into your applications or workflows.
Contact Us