Financial institutions can proactively track credit and debit card numbers for Dark Web exposure, enabling quick action to prevent fraud and bolster customer trust.
HOW IT WORKS
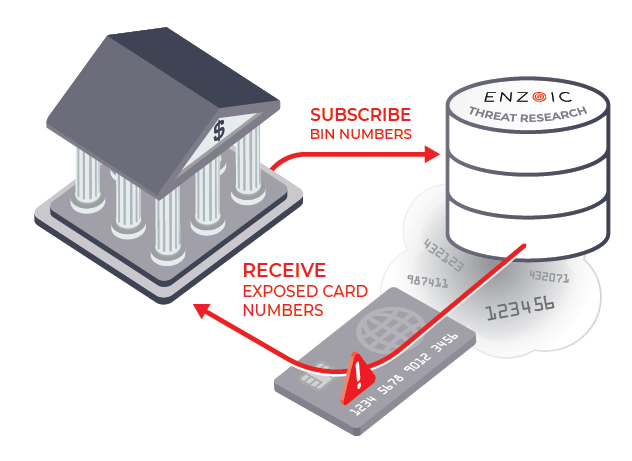
Enzoic’s Credit Card and BIN Monitoring enables financial institutions to subscribe their bank identification number (BIN), sometimes referred to as issuer identification number (IIN), for timely alerts if they’re circulating on the Dark Web. Through Enzoic’s intuitive service, an immediate alert with the full compromised card number is sent, allowing institutions to be proactive in their security approach and ensuring they are the first to detect compromised card data. Designed for flexibility, these alerts can be integrated with SIEM, card management, and other systems or workflows.
Download the Credit Card and BIN BriefHOW IT CAN HELP ME
A single compromised credit card costs issuers an average of $2,500. Bank identification number monitoring empowers financial institutions to proactively monitor credit and debit card BIN or IIN numbers for Dark Web exposure, enabling early remediation and damage prevention while enhancing customer security and trust.
FEATURES
Our threat research team ensures the most comprehensive and collection of compromised card data from the Dark Web.
Enzoic now employs AI-powered advanced language models to speed up the process of converting vast quantities of Dark Web data into useful and actionable information.
Financial institutions can take immediate action when breaches containing credit card numbers associated with their bank identification number or issuer identification number are found.
WHY ENZOIC
While VISA CAMs alerts inform you after potential fraud has already happened, Enzoic’s payment card monitoring leverages our continuously updated Dark Web database to deliver real-time alerts as soon as compromised card data is detected, ensuring quicker response times and the most comprehensive set of alerts. Enzoic’s alerts are highly customizable and integrate effortlessly with your existing systems through an easy-to-implement API, ensuring the right teams are notified promptly and can initiate automatic remediation.
No need for data queries or pulls. Enzoic seamlessly integrates into new or existing workflows for easy implementation.
Read the technical docs. Explore quick-start guides, code snippets, and a comprehensive resource library to integrate into your workflows.
Read Technical DocsBlake Rodemeyer, Director of Information Services
“We’ve entrusted Enzoic with the crucial task of monitoring the Dark Web for any potential exposure of our card numbers in 3rd party data breaches. It’s reassuring to know that we have a proactive system in place that keeps a vigilant eye on potential exposures, ensuring our members are protected from fraud.”
A BIN (also referred to as an IIN or issue identification number) is assigned to a bank for its own credit or debit card issuance and is usually the first four, six, or eight digits of a card number. The ISO Register of BINs for US banks and credit unions is managed by the American Bankers Association.
One of the primary ways credit card information can be leaked is through data breaches. Data breaches occur when unauthorized individuals gain access to secure databases and extract sensitive information, which can include credit card numbers, expiration dates, and CVV codes, among other personal data. These breaches can occur in all sectors including retail, finance, healthcare, and online services. Once the data is compromised, it can be sold, traded, or used for fraudulent activities, often appearing on the Dark Web subsequently.
A BIN attack is when a cybercriminal uses brute-force computing to guess and uses an accurate combination of a debit or credit card number, Card Verification Value (CVV), and expiry date. Once this has been completed and the fraudster acquires the right information, they use the card to commit fraudulent transactions in the cardholder’s name or sell the exposed cards on the Dark Web. A botnet can quickly test hundreds or thousands of combinations.
The exposure of card information through data breaches and BIN attacks poses severe challenges for issuers. Financial institutions bear the brunt of the consequences, facing both financial and operational repercussions. They are responsible for absorbing the cost of fraudulent charges resulting from BIN attacks, which includes not only the financial losses but also the associated operational and business costs. The repercussions extend to dealing with chargebacks, managing increased call center activity, and undertaking the process of card re-issuance.
Moreover, these breaches and attacks inflict damage on an institution’s reputation, leading to a loss of trust among cardholders and a resulting long-term impact on customer relationships. Additionally, financial institutions experience losses in interchange revenues, including less favorable interchange rates in a response to high amounts of fraud.
Once a compromised card is identified, financial institutions can take several immediate actions including blocking suspicious transactions, increasing scrutiny on the affected accounts, notifying the customer, reissuing a new card, and updating their fraud detection models. Moreover, the institutions can work with law enforcement agencies to address the compromise and investigate its origins.
Absolutely. Enzoic designed this service for flexibility and can seamlessly integrate into new or existing workflows, including SIEMs, card management, customer communication management, and even proprietary systems. This ensures minimal resource demands and allows for easy implementation within your existing security infrastructure.
Enzoic’s real-time alerting system notifies financial institutions the moment breaches containing debit and credit card numbers associated with their BINs are found. Financial institutions have used the alerts to create automated and tailored actions, including automatically disabling cards or notifying customers.
Resource Hub
Enzoic's new service will allow financial organizations to subscribe their institution's BIN to the service and receive alerts when it detects an exposure.
Blog
Financial institutions need to recognize the profound implications of third-party breaches and arm themselves with the tools and strategies.
Blog
Credential stuffing attacks are posing major risks to banks and credit unions. Read how to address the vulnerabilities in open banking.
Harnessing Dark Web intelligence to prevent attacks associated with compromised credit and debit cards.
Contact Us