Enzoic for Active Directory Lite is a free password audit tool that quickly identifies unsafe passwords.
See your domain’s password vulnerabilities in seconds.
Please review the EULA.*
Regular password audits are crucial due to the constant occurrence of data breaches that reveal user credentials. These passwords are quickly fed into hackers’ cracking dictionaries, resulting in the need for organizations to continually update the list of passwords that must be kept out of their systems.
Enzoic’s quick and free password auditor provides the most up-to-date credential-related information and reporting to ensure IT administrators have the most accurate and comprehensive picture in a simple clean dashboard.
HOW IT WORKS
Enzoic’s password audit tool is a lightweight version of the full Enzoic for Active Directory, an automated solution for keeping passwords secure.
Try the password auditor to quickly and easily identify compromised passwords. It will check against our threat intel database of 8+ billion exposed passwords.
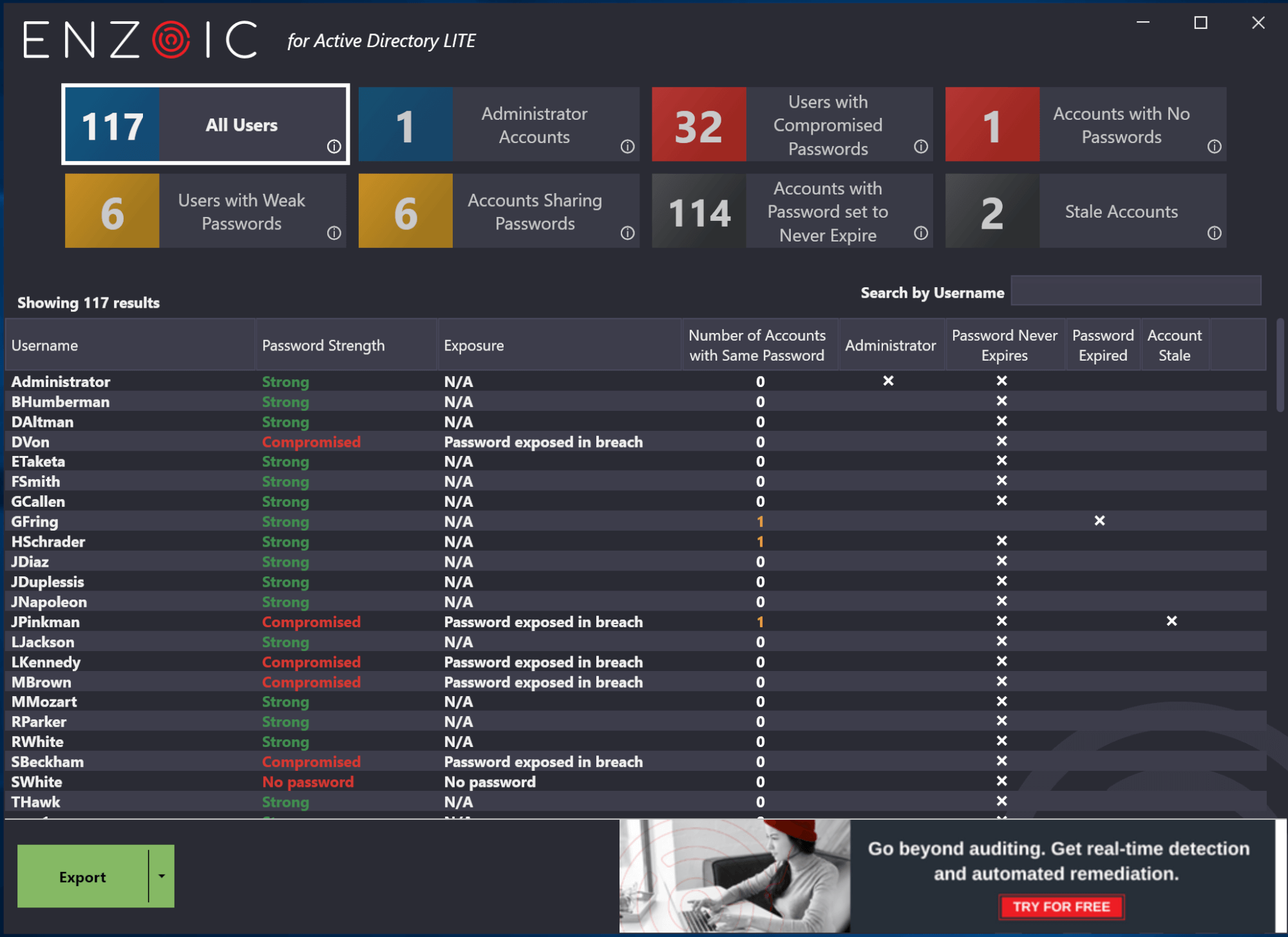
Uncover users with compromised, weak or common passwords, reused passwords, shared passwords, no passwords, passwords set to never expire and stale accounts.
Enzoic for AD Lite Password Auditor
Enzoic for Active Directory
The password audit provides a straightforward list of users in your domain, along with each individual’s compromise status. The data points collected include the number of administrator accounts, users with compromised passwords, accounts with no passwords, users with weak passwords, accounts sharing passwords, accounts with passwords set to never expire, and stale accounts
No license key is required for the password auditor. This is a free product.
Enzoic for Active Directory supports any 64-Bit Windows Client or Server. It can be run from any domain joined system using an account in the Administrators Group that can access the Internet.
Enzoic for Active Directory Lite evaluates passwords based on Enzoic’s database of 7+ billion compromised passwords and is updated several times each day. A database of this size could not be practically downloaded.
Enzoic rate limits the audit at 10 calls per second. Auditing a domain of 500 user takes about a minute. An audit of 10,000 users can be completed in under 20 minutes. That’s checking against a database of +8B entries!
Enzoic for Active Directory Lite uses a partial hash comparison approach through Enzoic’s Password API. This allows you to check whether a given password is known to be compromised, without the exact password or hash leaving your environment. It is only necessary to supply the first 10 hex characters of a hash. A list of candidate hashes will then be returned and compared locally with the exact hash to determine if there is a match. The partial hash data is not stored by Enzoic and is actively deleted from our server memory when this process is completed.
Enzoic collects two types of vulnerable passwords:
The full Enzoic for Active Directory is a complete solution for keeping vulnerable passwords out of your organization and complying with current NIST guidelines. It adds a customizable password policy within Active Directory to protect against unsafe passwords. It includes a custom password dictionary, blocks username derivatives, and checks fuzzy matches with common leetspeak substitutions. It then does automatic, continuous auditing to determine when a safe password becomes vulnerable. Remediation is also automated, including notification, password reset or disabling accounts. Learn more here
Explore free for up to 20 users. Save hours of admin time and simply get started.
Experience Enzoic