A series of simple, hosted REST APIs connected to our massive database of compromised credentials and accounts for integration into your application or website.
Try Now
HOW IT WORKS
An exposure is any unintended release of user credentials. This could be due to a data breach at a site, malware that has captured user credentials, a phishing site that has been capturing user credentials, etc.
Look up all the exposures for your users and obtain detailed information about each.
A compromised password is any password that has been found in a data breach or password cracking dictionary used by cybercriminals.
Check whether a password is unsafe.
A compromised credential is an exact username and password combination that has been found in a data breach, data exposure, or combo-list used by cybercriminals.
Determine whether a username/password combination is available to hackers.
HOW IT CAN HELP ME
Easily integrate our APIs to receive the earliest possible insight into data breaches or PII exposure, allowing you to mitigate damage caused by leaked credentials and remediate when customer or employee data becomes available on the Dark Web.
![]()
Get started with a free API key. With free plans up to 2,000 calls, our pricing is designed to scale with you.
While all of our APIs are callable directly, by far the easiest way to get started using Enzoic is to use one of our rich suite of libraries that you can use within your applications. We offer a series of Quick Start tutorials for each.
Our APIs give you multiple options for proactively avoiding exposure.
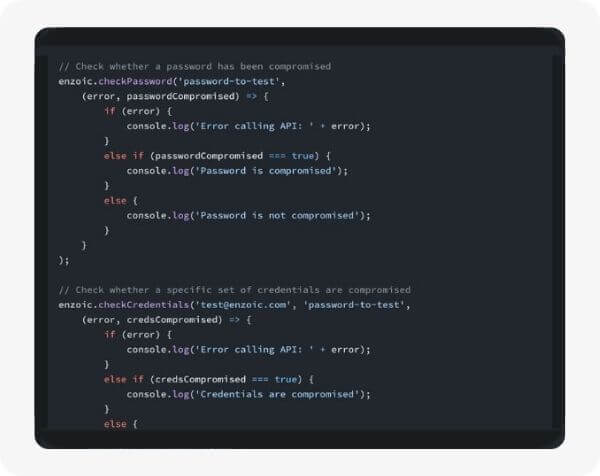
Explore quick-start guides, code snippets, and a comprehensive resource library to integrate into your workflows.
Read API DocsTim Nufire, Founder & Chief Cloud Officer
“We’re impressed with Enzoic’s creative approach to catching credential stuffing attacks using their database of compromised credentials as a proactive defensive against ATO. Enzoic does this securely without cracking hashed passwords or being given access to our users’ credentials and doesn’t add unnecessary steps to our customers’ login process.”
Calls
Free for up to 2,000 Calls!
First 2,000 Calls: $0 / Call Next 3,000 Calls: $0.040 / Call Next 5,000 Calls: $0.020 / Call Next 40,000 Calls: $0.015 / Call Next 50,000 Calls: $0.010 / Call Next 100,000 Calls: $0.008 / Call Next 800,000 Calls: $0.005 / Call Over 1M Calls: Contact Us
Contact Us
Billing Cycle
-
Monthly
Custom
Payment Methods
-
Credit Card
Custom
Max Calls
2,000
1,000,000
Custom
Support
Self-Service / Knowledge Base
24-hour response during business week
4-hour response during business week
SLA
-
-
Custom
Passwords API
Credentials API
Exposures API
Cleartext Credentials API
-
-
Blog
Attackers can use compromised credentials to gain unauthorized access to an organization's information, leading to ATO attacks.
Blog
Ensure GDPR Compliance and Protect Your Organization from Costly Penalties. Learn the key steps to take when handling EU citizens' data in the event of a data breach.
Blog
Credential stuffing attacks are posing major risks to banks and credit unions. Read how to address the vulnerabilities in open banking.
We make it easy to try, implement and protect. Start building for free.
Experience Enzoic