Eliminate compromised passwords in AD. Enzoic for Active Directory is an easy to install plugin that gives you a frictionless way to identify, monitor, and remediate unsafe passwords and credentials.
Try Now
HOW IT WORKS
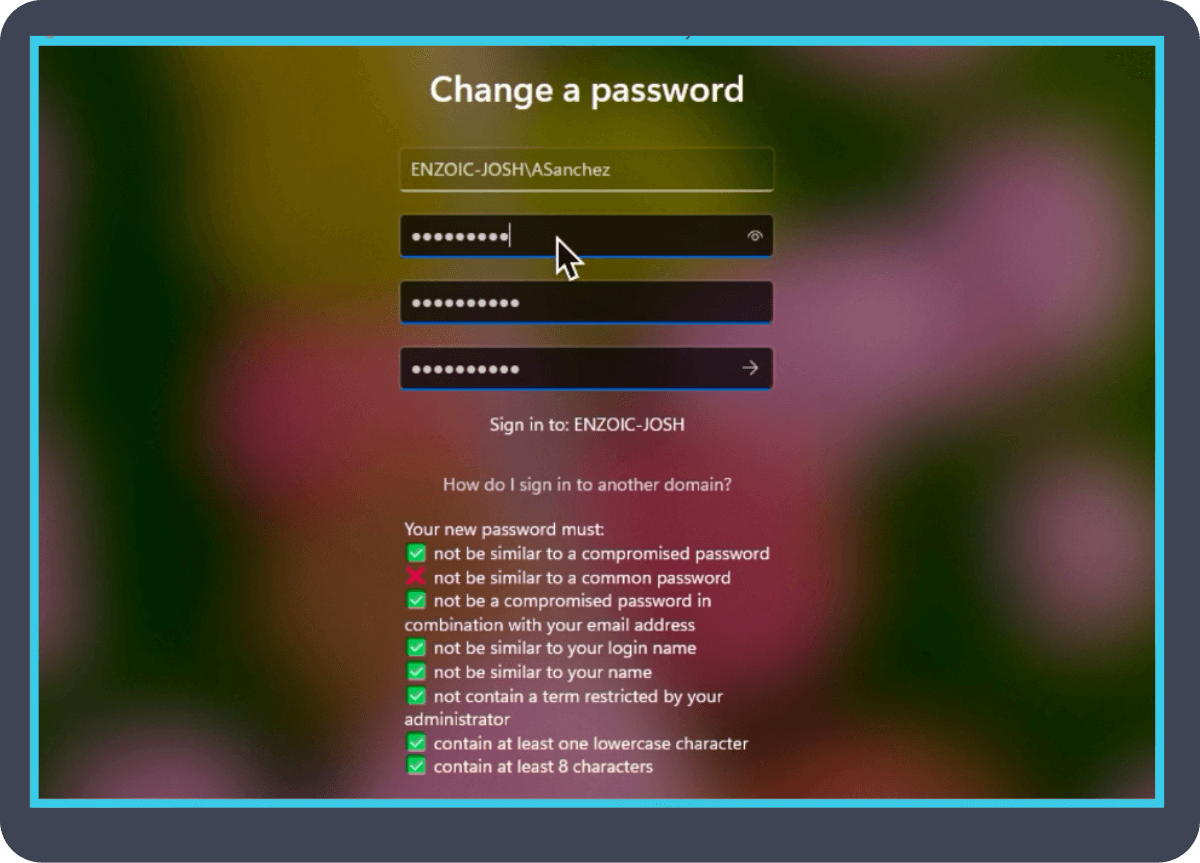
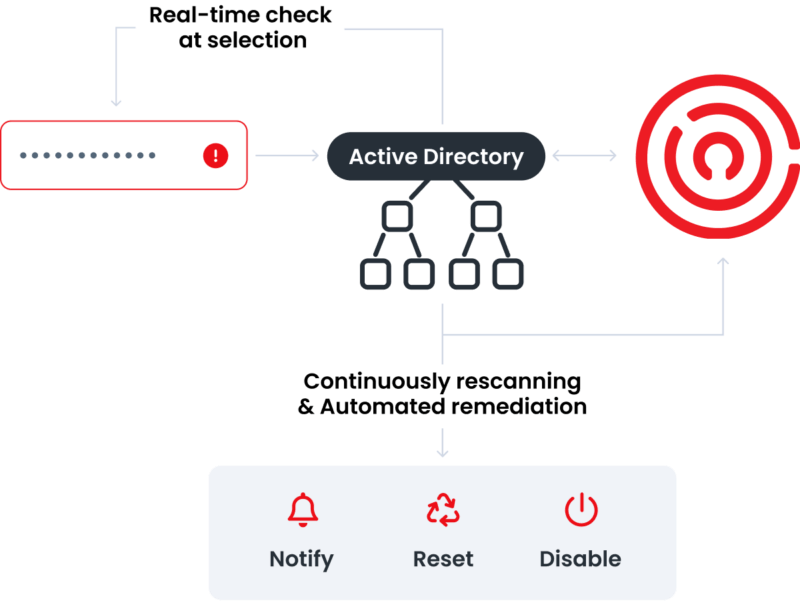
Enzoic for Active Directory’s password monitoring ensures that new passwords comply with a configurable password policy every time a password is created. These username and password credentials are continuously monitored against our active threat collection database for exposure by sending a partial hash to Enzoic’s database for comparison, which then exports full hashes of likely matches locally for analysis so sensitive data never leaves your environment.
When a user’s information is detected in a data breach, Enzoic automates remediation with a variety of configurable actions that include requiring a password reset or disabling an account.
HOW IT CAN HELP ME
Enzoic for Active Directory is an end-to-end solution that can align with your needs.
Download One-pager![]()
System admins can operate efficiently with customization options and remediation controls that align to your needs.
![]()
End time-based password resets and reduce help desk call volume by quickly and automatically responding to exposed credentials.
![]()
With a click of a button, Enzoic for Active Directory can meet all the NIST password policy guidelines.
FEATURES
Enzoic for Active Directory’s password monitoring makes it easy to protect your organization against the #1 cause of a data breach: compromised credentials. Save time while enhancing security by eliminating periodic password resets and complying with NIST standards.
Enzoic for Active Directory prevents compromised passwords from being used within your organization. It’s a cybersecurity solution built from the ground up by technology experts based on current industry best practices and NIST guidelines. Watch the video to learn more.
For technical details, reference documentationCredentials that were safe yesterday may not be safe today. We help you identify, act, and remediate fast. By screening username and password pairs at creation and monitoring them on a daily basis, we’re giving organizations a leg up in their battle against account takeover.
Enzoic’s proprietary database is powered by real-time human and automated threat intel, giving you the comfort of a compliant and safe organization.
Enzoic for Active Directory can help you enhance security, create a better user experience, save time, and reduce admin costs. Most users can install and configure in 15 minutes or less.
With compromised credentials being the top cause of data breaches, protecting passwords is critical. Many organizations rely on Microsoft Entra ID (formerly Azure Active Directory) for password security, but it has notable limitations, especially in hybrid environments.
For robust, proactive password protection, Enzoic outshines Entra ID by addressing these critical gaps and securing your accounts against modern threats.
Peter Rio, IT Network Manager, Management Information System
“We selected Enzoic for Active Directory because it automates compliance with the NIST password guidelines and it can be installed in just a few minutes. It includes continuous exposed password filtering and if bad passwords are found, remediation is automated so it does not create any additional work for our IT team. The custom local dictionary enables us to block our company name, product names and some of the common words our employees may choose to use. The experience is seamless for our users. It only impacts the users that are using bad or exposed passwords, all other accounts are protected without any additional friction.”
David McCue, Information Technology Manager
“Employees will always find the easiest way to use their passwords so you should implement solutions that prevent threat actors from exploiting the resulting vulnerabilities. Enzoic is a great tool that ensures password security without needing any additional employee training or adding an administrative burden on IT. Now that I know our employees are utilizing more secure passwords, I sleep better at night!”
Users
Free for up to 20 Users!
First 20 Users: $0/User Next 80 Users: $1.50/User Next 300 Users: $1.00/User Additional Users: $0.75/User
First 20 Users: $0 / User Next 80 Users: $2 / User Next 300 Users: $1.33/ User Additional Users: $1.00 / User
Starting at $495 / month
Billing Cycle
-
Monthly
Monthly
Custom
Payment Methods
-
Credit Card
Credit Card
Custom
Max Users
20
Unlimited
Unlimited
Custom
Support
Self-Service / Knowledge Base
24-hour response during business week
24-hour response during business week
24-hour response during business week
SLA
-
-
-
Custom
Screen User Password Changes
Continuous Password Protection
Branded User Alerts
One-Click NIST 800-63B Compliance
Full Credentials Monitoring
-
Multiple Monitoring Policies
-
Blog
Active Directory is a prime target for threat actors and companies must act now to eliminate it as a threat vector. Here’s why, and how.
Blog
Microsoft’s password protection doesn’t check any available lists of compromised passwords or the vast majority of blacklisted passwords.
Resource Hub
Understanding MFA limitations and how integrating it with other robust security measures is crucial for building a truly resilient defense mechanism.
Explore free for up to 20 users. Save hours of admin time and simply get started with a password monitoring solution.