Enzoic for Active Directory 3.6 is now live, delivering both usability upgrades and deeper security insights. This release makes it easier for users to pick safe passwords and gives admins richer visibility into credential risk. Key highlights of version 3.6 include:
These enhancements work together to streamline password resets and incident response. The Windows client now shows live policy guidance so users can see which rules are met (green ✅) or unmet (red ❌) as they type. Behind the scenes, Enzoic continuously checks against breach data and policy rules. If a password is rejected (for example, because it matches a previously breached password) the client explicitly tells the user which policies are unmet with each keystroke. This instant guidance makes it much simpler for employees to create a compliant, secure password on the first try, reducing guesswork and help-desk calls.
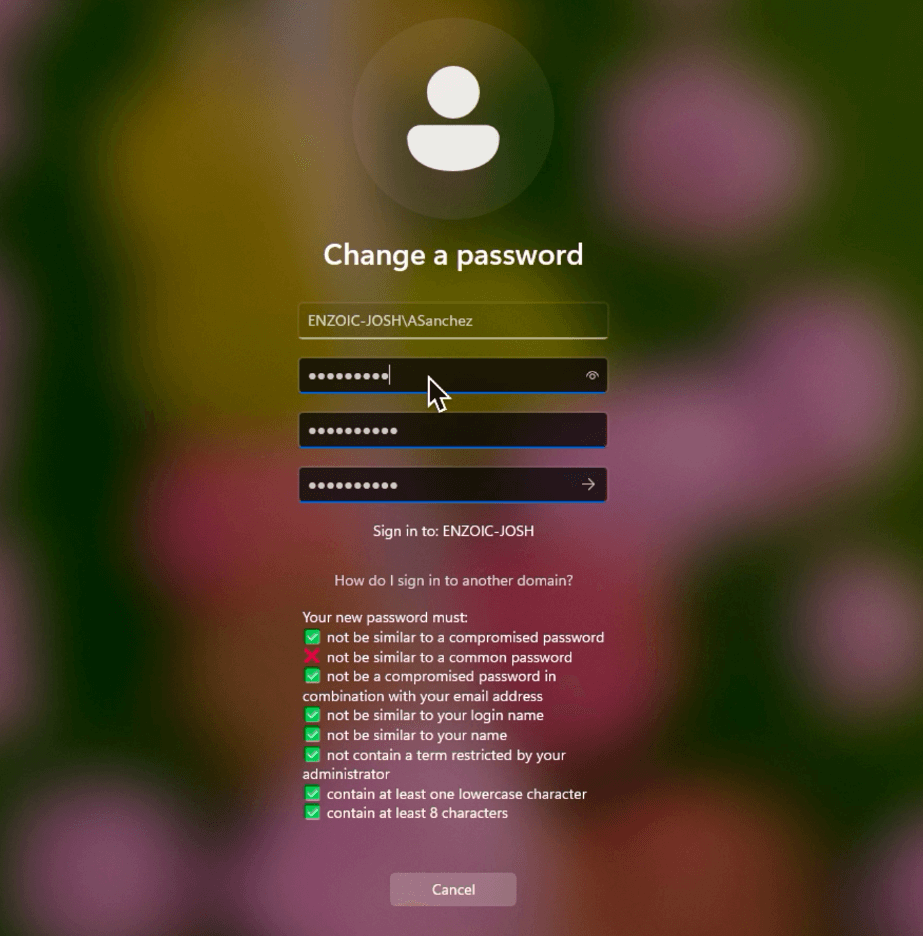
Figure: The Windows password change screen now shows Enzoic’s live feedback. As the user types, policy rules and breach checks update instantly.
In version 3.6 the Windows client provides “as-you-type” feedback right on the standard password-change dialog. In the screenshot above, you can see how Enzoic displays a checklist of password rules. A green check mark (✅) means the password meets that rule, and a red X (❌) means it doesn’t. As the user types each character, the list updates in real time. This immediate feedback guides users to choose a password that’s both safe and compliant, avoiding frustration.
If a password is blocked, the client now explains the rejection. For example, if the password is found in a breach database, Enzoic will explicitly notify the user that the new password is compromised. Likewise, if it violates a company policy rule (too short, contains a forbidden word, etc.), the client highlights which rule was broken. By surfacing the exact reason for any rejection as they type, users understand the problem and can fix it on the spot. In practice, this clarity reduces helpdesk tickets and speeds up resets, since employees spend less time guessing or calling support.
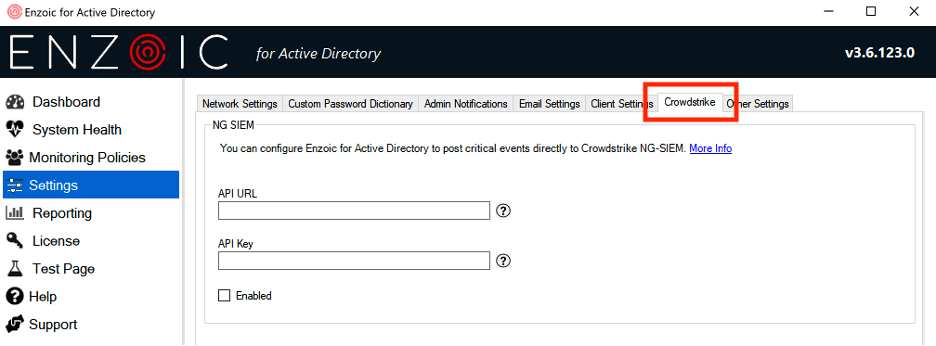
Figure: Enzoic’s new CrowdStrike integration settings. Enzoic can send credential-risk events directly into CrowdStrike Falcon NG-SIEM.
Another major upgrade in 3.6 is with CrowdStrike Falcon NG-SIEM. Enzoic can now feed password-risk alerts straight into the CrowdStrike Falcon platform. In the product console (pictured above), administrators simply enter the Falcon API URL and key to enable the integration. Once set up, any time Enzoic detects a compromised or out-of-policy password, an alert is pushed into CrowdStrike.
This unified approach means security teams see password breach alerts alongside endpoint and network data, all in one panel. For example, if an account’s password shows up on a breach list, CrowdStrike can correlate that credential alert with recent endpoint activity (login times, locations, suspicious processes, etc.). By bringing credential intelligence into the Falcon NG-SIEM, analysts save time: they no longer have to switch between tools. Instead, they get full visibility into compromised credentials in context. This works in tandem with Enzoic’s automated remediation for faster root-cause analysis of account-based threats.
Enzoic 3.6 also makes password issues crystal clear in reports and dashboards by separating “compromised credentials” from “out-of-policy passwords.” In previous versions these flags could fall within the same category in some instances; now each is explicitly labeled on the main dashboard and in the reporting. Administrators and users can immediately see why a password was flagged:
The Compromised Users report in the console now lists accounts with either out-of-policy or compromised passwords and it clearly identifies which category applies.
Enzoic for Active Directory 3.6 is a must-have update for both users and security teams. It transforms the password change experience with live guidance and gives administrators detailed, actionable data. Existing customers are encouraged to upgrade to 3.6 as soon as possible to take advantage of these improvements. New users can start a free trial of the Enzoic AD console and see the version 3.6 features in action.
For more information, visit Enzoic’s product page or contact our team.
AUTHOR
 Josh Parsons
Josh Parsons
Josh is the Product Manager at Enzoic, where he leads the development and execution of strategies to bring innovative threat intelligence solutions to market. Outside of work, he can be found at the nearest bookstore or exploring the city’s local coffee scene.
Stop Compromised Credentials and start exploring for free – up to 20 users or 2000 API calls.