Active Directory environments use Kerberos as the default authentication protocol, which unfortunately makes them particularly vulnerable to “Kerberoasting”, an attack where threat actors leverage the fact that service tickets are encrypted using a key derived from the account’s password to obtain the credentials and takeover privileged accounts. Generally, the adversary performs a service ticket request for a target account using its Service Principal Name (SPN), captures the returned ticket, which is encrypted using the service account’s NTLM password hash, and then uses offline hash-cracking techniques to guess the plaintext password. If successful, the attacker can then log in with the account credentials, and gain full control of that service account and any privileges it holds. In practice, any domain user (even with no special rights) can perform this: they simply enumerate SPNs in AD, send a TGS-REQ to the Key Distribution Center (KDC) for a target SPN, and receive a TGS-REP encrypted by the service account’s key. Kerberoasting has been reported in many cyberattacks, including one of the largest healthcare data exposures of all time, the 2024 Ascension ransomware breach. As the core of this vulnerability is password strength (that is, whether or not attackers can crack a password hash), enormous data breaches like this emphasize the need for strong passwords.
Kerberoasting unfolds in several automated steps that abuse Kerberos’s normal ticketing process:
Since Kerberoasting requires an attacker to authenticate as a domain user to request service tickets, protecting all user (including service) accounts from compromise denies that prerequisite and effectively blocks the attack. Additionally, the attack succeeds only if the password hash is crackable. Thus, enforcing long service account passwords in accordance with NIST guidelines and preventing use of exposed credentials directly undermines it. The 2024 Ascension Health incident is a prime example; attackers obtained privileged access through Kerberoasting of service accounts. Preventing even one compromised service password can break the attack chain, which is precisely what Enzoic’s AD solution aims to do.
Enzoic for Active Directory installs as a password filter on your domain controllers, intercepting every password set or change. It enforces a configurable policy and immediately checks each new password (via a partial hash) against Enzoic’s live database of breached credentials. If a chosen password is too simple or appears in a data breach, the filter will block the change or flag it for remediation. This means no new service account password can be weak or already-compromised; each must satisfy your policy (length, complexity, etc.) before being stored.
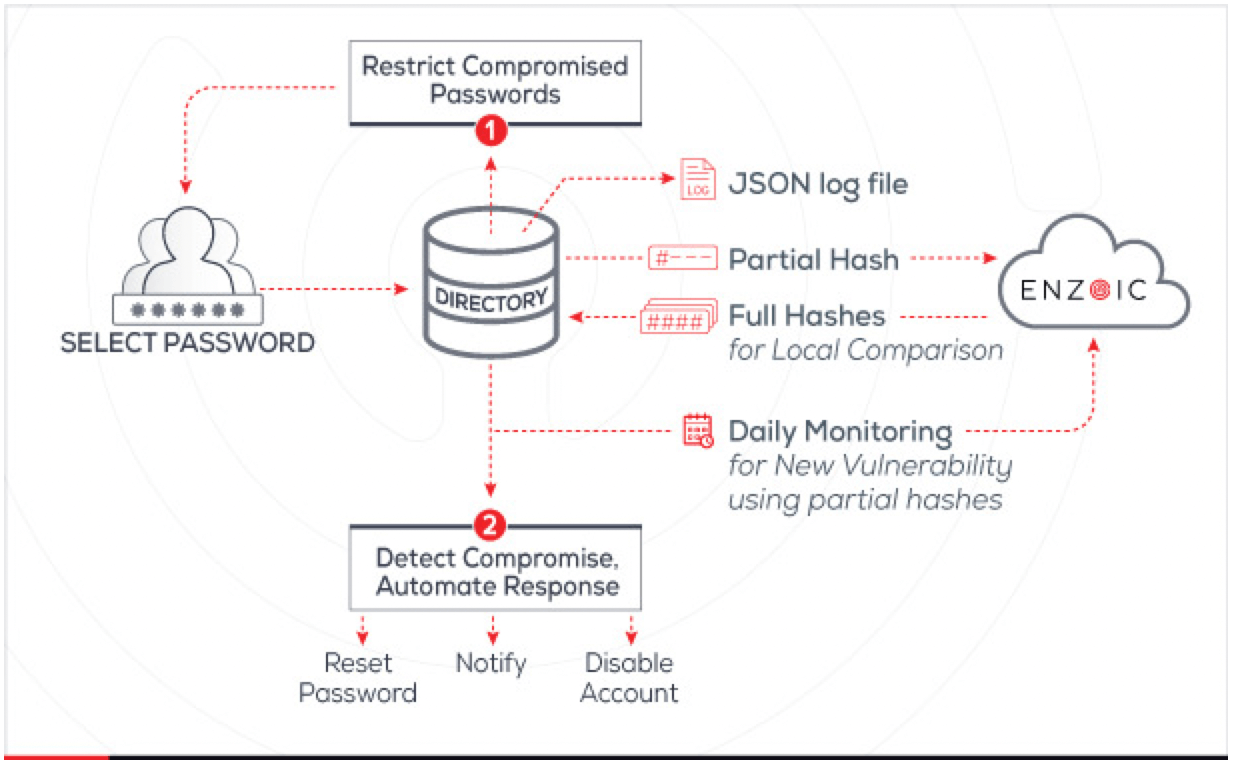
The figure above illustrates this flow: as soon as an admin attempts to set a password on AD, Enzoic validates it in real time, then continuously scans credentials afterward. For example, if someone tried to set a service account password that was present in an external breach, Enzoic would immediately reject it or require a reset, preventing the attacker from obtaining a vulnerable hash that’s already been compromised and likely to be cracked or correlated to the correct password. By vetting each credential up front, Enzoic closes the window that Kerberoasting relies upon.
Credentials that were safe yesterday may be breached tomorrow. Enzoic continuously monitors all AD credentials (usernames + passwords) against the latest breach intelligence. Every day (or even in real time) it scans your domain’s accounts by sending partial hashes to the Enzoic cloud and checking for matches. If an account’s credentials show up in a new leak or blacklists, Enzoic can automatically trigger remediation (for example, forcing an immediate password reset or disabling the account). In practical terms, if an attacker leaks a service account’s password on the dark web, Enzoic will catch it before it is exploited in Kerberoasting. Administrators can configure automated actions so that compromised accounts are locked down or require re-authentication.
Enzoic’s continuous scanning covers every account indiscriminately. That means even long-established service accounts without recent password changes get re-evaluated against fresh intelligence. The platform checks likely hash matches locally for analysis, ensuring sensitive data never leaves your network. In one click, Enzoic aligns with NIST guidelines, it can force character minimums on all accounts and prevent reuse, then watches for any exceptions over time. The combination of proactive blocking at reset and proactive alerts if a credential shows up in a breach gives organizations a “second chance” to stop Kerberoasting. Attackers lose the advantage of time: even if they capture a service ticket today, by tomorrow that account might already be disabled or its password changed before they complete cracking.
Service accounts (especially those with SPNs) often have long-lived passwords. Enzoic lets you make those passwords as strong as possible. Administrators can set granular complexity rules (minimum length, required character classes, blocked patterns, etc.) on any AD group, OU, or user type. For example, you can enforce a minimum character length for all SPN-enabled accounts and disallow use of any word in a company dictionary or user names. Enzoic even supports “root password detection” rules and detects variations of common words. This prevents easily crackable secrets from ever entering AD.
Enzoic seamlessly integrates these rules: it has one-click NIST 800-63B compliance, which means it can enforce that new passwords have not been previously compromised without impacting operational friction. In practice, this drives service account passwords into a realm where offline cracking is computationally infeasible. If every SPN account has a secure password with no compromised values, a Kerberoaster’s Hashcat will exhaust resources long before it succeeds. In combination with the breached-password checks above, this ensures service credentials are uncompromised at creation and remain uncracked, the core requirements for Kerberoasting protection.
Enzoic doesn’t just enforce policies silently; it logs every event for audit and SIEM. The product emits structured JSON events for actions like password changes, failed changes, and detected compromises. Key events include PasswordChangeRejected (when a new password fails policy or is known-bad) and CompromiseDetected (when an account’s credentials are found in a breach). These can be ingested by any SIEM or log management system. In fact, Enzoic provides a generic JSON log file and direct integrations. For example, you can push Enzoic’s audit stream into CrowdStrike Falcon’s NG-SIEM module.
With this data in your SIEM, security teams gain visibility into Kerberoasting-related activities. For instance, repeated “PasswordChangeRejected” events for a service account could indicate someone trying to weaken the password, while a “CompromiseDetected” alert confirms that a previous password is unsafe. By correlating Enzoic’s logs with AD audit logs (like unusual TGS-REQ request patterns), a SOC can detect and respond to early signs of Kerberoast attempts. In short, Enzoic closes the loop: not only does it prevent weak or breached credentials, but it also surfaces any policy violations or exposures in SIEM dashboards and reports. This integration ensures that Kerberoasting becomes a trackable event rather than a silent exploit.
Enzoic for Active Directory therefore layers on top of native AD controls to provide end-to-end Kerberoasting protection. It intercepts passwords at creation, relentlessly hunts for any leaks afterward, and enforces uncompromised passwords, complexity rules, and a minimum length on service accounts. When every credential in the domain is screened and monitored this way, the probability that an attacker can extract and crack a service account hash drops to near zero. In practice, organizations using Enzoic see far fewer Kerberos-related escalations, especially compared to relying on static AD policies alone.
AUTHOR
 Josh Parsons
Josh Parsons
Josh is the Product Manager at Enzoic, where he leads the development and execution of strategies to bring innovative threat intelligence solutions to market. Outside of work, he can be found at the nearest bookstore or exploring the city’s local coffee scene.