Now Is the Time To Contribute Your Feedback on the NIST Privacy Framework
A full four years have passed since the NIST Privacy Framework, titled ‘A Tool for Improving Privacy Through Enterprise Risk Management, Version 1.0,’ first made its mark. In the time since its debut, numerous organizations have discovered its immense value in shaping and refining their privacy initiatives. Moreover, NIST Special Publication (NIST SP) successfully expanded the framework’s utility by integrating a diverse set of resources to aid in its deployment. As a non-regulatory agency and science lab, the National Institute of Standards and Technology (NIST) continues to drive innovation in measurement science, offering guidelines for organizations, information systems, and federal agencies to balance data utilization and individual privacy.
The concept that measurements, regulation, compliance, and best practice guidelines can foster innovation may seem a little bewildering to some people. Most people assume regulation hinders innovation. NIST lists that their real central mission is to enable innovation. The idea is that if you know how to measure something, then you know how to design it, and once you have designed it, you can improve it. This balancing act between innovation and structured guidelines has been a hotly debated topic in the tech world. However, the ultimate goal is to strike a balance where innovation flourishes at the same time as proactively protecting the rights and concerns of individuals in the digital age. This privacy framework is another part of the picture and an opportunity for you to share input on the right balance.
Documents of this type function more as guidelines rather than a rigid checklist that all organizations should follow. While this approach leaves more room for flexibility and innovation, it can leave some companies confused about the best way to tackle the privacy issues their organization faces. The level of adherence that organizations will need to exercise in relation to these guidelines will be determined by the relevant laws that they must adhere to, their own internal policies, or if they have any contractual obligations to meet certain NIST standards.
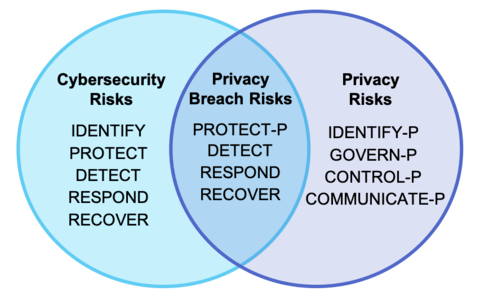
The NIST Privacy Framework aims to present existing practices and suggests ways to effectively strengthen individuals’ privacy through new practices. The document is designed to work in parallel with NIST’s Cybersecurity Framework so organizations can better manage the risks of privacy in an increasingly privacy-conscious age.
The Privacy Framework can drive better privacy processes and help organizations protect individual privacy through these three objectives outlined in the executive summary:
The NIST Privacy Framework can drive better privacy processes and help organizations protect individual privacy through these three objectives outlined in the executive summary:
We would like to offer some suggestions and clarity around the NIST password guidelines under the “Protect-P” part of the draft.
Privacy Breach Risk 1: Compromised or Weak Passwords
As part of the NIST Digital Identity Guidelines, NIST put forward recommendations for organizations to screen new passwords against known compromised passwords. This process is known as credential screening in the case where both the username and password are screened. Or it is password screening, in the case that only the password is filtered. It is an integral part of the “Detect” function in the NIST Privacy Framework baseline.
Implementing this type of screening can significantly increase the information security of an organization. Attackers put considerable effort into hacking into systems and stealing sensitive information. Attackers use this data to gain access to a customer’s other online accounts or to gain access to corporate networks.
Cybercriminals rely on commonly used passwords or exposed passwords to successfully conduct brute force or credential stuffing attacks to gain access. Successful data breaches that leak usernames and passwords have become an alarmingly common reality of the digital age. It has gotten to the point where it’s unusual to go a single day without a significant data breach occurring.
These exposed usernames and passwords end up on databases on the dark web where other cybercriminals can buy or utilize them. There are billions of credentials on the Dark Web and public Internet. (Check out a sample password on www.enzoic.com/password-check to see if your password is exposed. Test out other passwords that you think could be safe and witness the scale of the problem.)
Password screening, as part of the security controls, prevents users from reusing passwords that have been exposed, are weak, or are common. Attackers hope that most people are too lax about their security to change their passwords or create a unique one for every account. They also know that people are predictable, and they will follow common patterns when choosing their passwords. Passwords like “123456,” “password,” or “qwerty” may be funny and easy to remember, but they are also the first ones a cybercriminal will try in a brute- force attack.
By introducing screening for compromised or weak passwords, organizations can dramatically increase password security and maintain the privacy of data in their environment.
Privacy Breach Risk 2: Password Storage
Companies can store passwords in PlainText, encryption, or hashing formats, with hashing recommended for its security. PlainText storage is highly insecure, making breaches straightforward for hackers, and has led to notable companies experiencing breaches. Encryption offers more security by disguising passwords with a key, but it’s vulnerable if the key is compromised. Hashing is the safest, transforming passwords into a fixed-length string that’s hard to reverse-engineer, though not infallible. Security with hashing, like B-Crypt, evolves to stay ahead of hackers’ abilities to crack algorithms. Adapting to technological advancements is crucial for maintaining security.
Privacy Breach Risk 3: Partial Hashing vs. Hashing
This third area refers to factors addressed in the first two above.
When it comes to credential and password screening, many screening products will crack the password input by the user. This cracking creates a significant security risk because it makes the password known to more parties. If the goal is to create secure, private, and strong passwords, then there shouldn’t be a process designed to reveal a full password. It also represents a privacy issue. Users often assume that their password is being protected by the organization with which they are transacting. They would likely not appreciate knowing a 3rd party has cracked their password on behalf of that organization and stored it in cleartext.
The cybersecurity field is attempting to move to models where a password would only be known by the user who created it. When done correctly, this means that an organization’s IT team wouldn’t even be able to view the password. Additionally, third-party software shouldn’t be able to view the password either. Each time a password is revealed, it creates a new weak link or area of vulnerability that can be exploited by attackers or by internal bad actors.
Partial hashing is a better option. Credential screening products that use a partial hash approach are preferred because they are more secure and protect a user’s privacy. In a partial hash approach, only part of the password hash will be used to check if the password has been compromised. For example, the software may use the first and last five characters of the password hash to check how secure the password is. This method protects the full password from being known, thereby vastly reducing vulnerability.
Reflecting on the significant progress achieved with the NIST Privacy Framework since its first release, the tech community is now witnessing an exciting phase of evolution with the development of Version 1.1. This update is not just a testament to the framework’s success but also a response to the dynamic landscape of technology and cybersecurity. With the recent launch of the NIST AI Risk Management Framework (AI RMF) and the initiation of updates to the NIST Cybersecurity Framework (CSF) towards Version 2.0, the need for a refreshed and more integrated Privacy Framework has become evident.
The NIST Privacy Framework 1.1 is being designed as a versatile and adaptable tool, intended to evolve in alignment with stakeholder requirements and emerging technological trends. Originally developed in conjunction with the CSF for seamless integration, Version 1.1 aims to maintain this synergy, incorporating necessary adjustments to align with the advancements in CSF 2.0. This iteration will focus on targeted improvements identified by stakeholders over the years, enhancing the framework’s effectiveness and ease of use in the current privacy risk management context.
Additionally, recognizing the increasing need for holistic approaches in managing data across various domains, NIST is exploring the creation of a Joint Frameworks Profile for Data Governance. This innovative concept emerged from discussions with stakeholders who highlighted the foundational role of data governance in managing privacy, cybersecurity, AI, and IoT risks. The envisioned Profile could manifest in various forms, like a flow chart or a crosswalk among NIST Framework Subcategories, to illustrate the effective use of NIST frameworks and resources in a cohesive manner. The development of this Profile will be an integral part of the Privacy Framework 1.1 update process, involving the same community of stakeholders and experts.
Robust password requirements and storage policies are a crucial way we protect an organization’s systems, but it is also critical for a privacy policy. This framework is a significant step forward in protecting user privacy while leveraging parts of the NIST Cybersecurity Framework.
We encourage everyone to read through the NIST Privacy Framework.
Start for free. Enzoic provides a clean user interface to screen for compromised passwords.
Experience Enzoic