Make NIST password compliance simple. NIST 800-63B Digital Identity Guidelines call for checking new passwords against cybercriminal dictionaries.
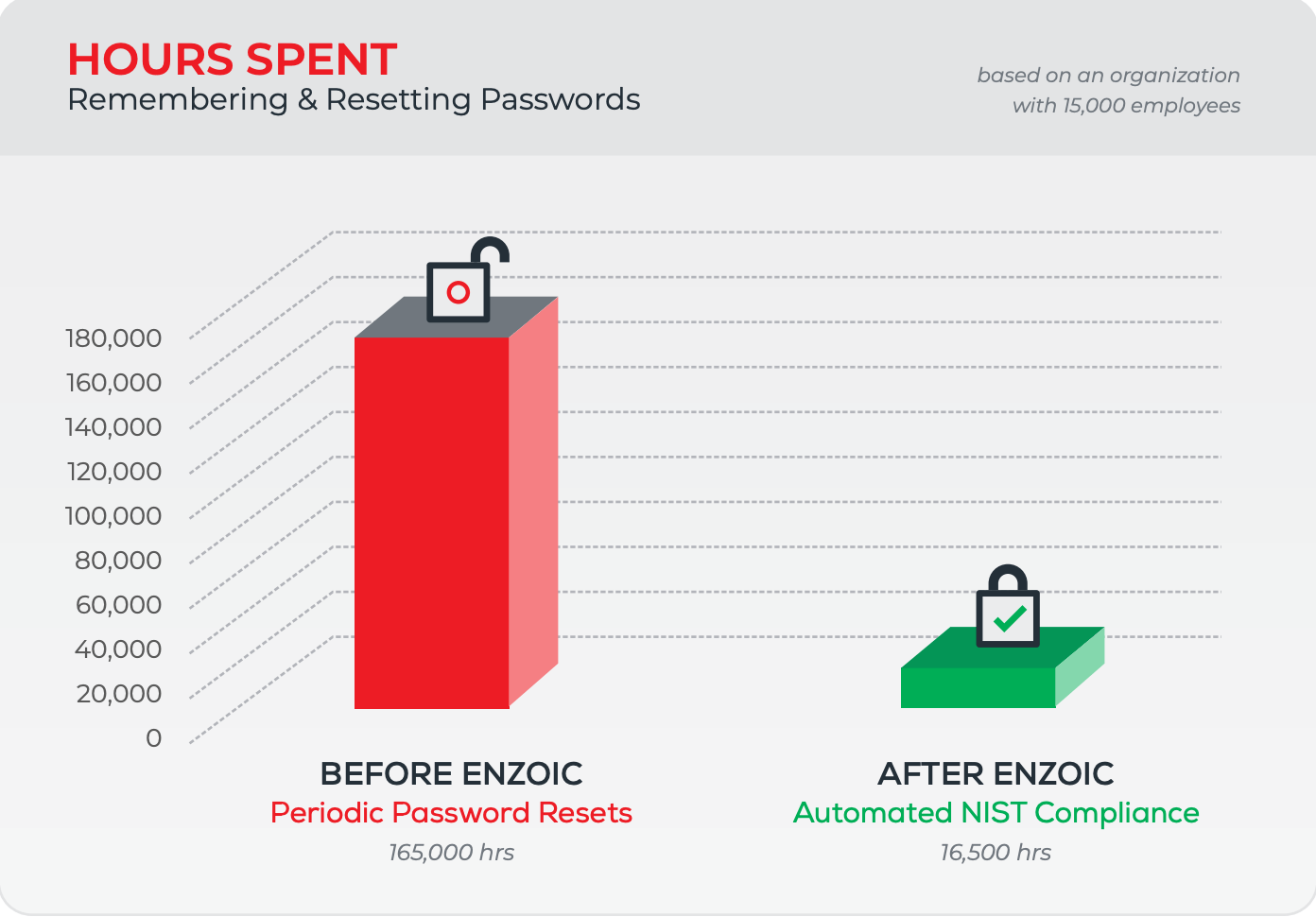
Start for FreeMultiple studies have shown requiring frequent password changes is actually counterproductive to good password security.
No more arbitrary password complexity requirements needing mixtures of upper case letters, symbols and numbers. Like frequent password changes, it’s been shown repeatedly that these types of restrictions often result in worse passwords.
One of the best ways to ratchet up the strength of your users’ passwords is to screen them against lists of dictionary passwords and known compromised passwords.
OVERVIEW
NIST encourages organizations to monitor new passwords daily to prevent the use of commonly compromised credentials. The NIST 800-63B password compliance continuous enforcement improves both security and usability.
People follow very common patterns in password selection, even when a written password policy is in place. Bad actors use lists of common passwords and patterns found in previous breaches to narrow the universe of passwords attempted in their attacks. Guessing passwords becomes easier when the actual set of passwords is predictable.
HOW IT WORKS
Enzoic continuously collects compromised passwords and aggregates cracking dictionaries to maintain a comprehensive, constantly updated blacklist of unsafe credentials. This list contains billions of entries sourced not only from historical breaches, but also from the Dark Web, Deep Web, and infostealer malware logs. Our Threat Intelligence team monitors emerging attacker tools and tactics to ensure new exposures are added as quickly as they appear.
Meeting NIST’s password compliance requirements becomes straightforward with Enzoic. Our researchers curate unsafe passwords from breached datasets, cracking dictionaries, and underground sources, then deliver them through our Active Directory plugin and RESTful API, making it easy for organizations to screen and block unsafe credentials.
NEW NIST UPDATE
The recently released NIST 800-63B Rev 4 introduces refinements to password compliance requirements:
Enzoic makes adopting NIST 800-63B Rev. 4 updates seamless with automated enforcement in Active Directory. Explore the latest password updates.
HOW IT HELPS ME
Adopting a NIST password policy improves user experience by eliminating password complexity rules and reducing frequent password resets. It lowers IT administrative costs by cutting password reset calls and automated remediation. It also improves security by following modern industry recommendations for passwords.
NIST password compliance:
Saving Time and Strengthen Security
The National Institute of Standards and Technology is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST develops cybersecurity standards, guidelines, and best practices to serve US-based industry and US federal agencies.
NIST’s Digital Identity Guidelines (Special Publication 800-63B) offer dependable recommendations for managing identity and access, including the establishment of effective password guidelines and password policies. These guidelines are widely adopted across industries and organizations as a security standard. It also helps organizations with cyber insurance requirements
Yes, the NIST guidelines recommend comparing passwords against known breach databases and common dictionary words to identify and reject compromised credentials. This proactive approach helps organizations prevent unauthorized access and mitigate security risks.
Enzoic for Active Directory enables one-click compliance by continuously screening for weak, expected, and compromised passwords, ensuring automated NIST password compliance with minimal admin overhead.
Many tools claim to help with NIST password compliance, but they rely on static blacklists or only check passwords at creation. Enzoic continuously screens every password in Active Directory against billions of compromised credentials, updated daily. This ensures organizations achieve true continuous NIST compliance instead of one-time checks, reducing their risk of credential-based attacks.
Blog
NIST password guidelines have real-world applications in every organization. Here's what you can do to stop your passwords from being compromised.
Blog
Understanding the Role of NIST IA-5 in SP 800-53. One essential aspect is the Control Enhancement IA-5 for password-based authentication.
Blog
See how CMMC and NIST password compliance align. Why it matters for DoD contractors, and how Enzoic helps block weak & compromised passwords.
Start for free with Enzoic and enable automated NIST 800-63B compliance in Active Directory.
Experience Enzoic