Insights from Enzoic’s AD Lite Data
Compromised user credentials are a major security threat for organizations, as the 2025 Verizon DBIR reported that credential abuse was the leading initial access vector for data breaches. Recent data from Enzoic’s Active Directory Lite (AD Lite) tool indicates that the risk of compromised credentials is growing. Analysis of aggregated AD Lite scan results for 2024 and 2025 shows credential-related risk becoming more pronounced across organizations. Not necessarily because users are choosing worse passwords year over year, but because the volume of exposed credentials is rising sharply as data breaches continue to accelerate. In other words, even when users keep the same passwords, they are increasingly likely to become compromised as breach datasets expand.
Shortcomings like weak passwords, password reuse, and inactive (“stale”) accounts are contributing to a larger share of users being vulnerable to account compromise.
In 2025, AD Lite domain scans averaged 1,014 users. While some environments were substantially larger or smaller, the average compromised-password rate was about 19% (196 compromised-password users out of 1,014 users per domain, on average), illustrating that exposure remains significant across organizations of many different sizes.
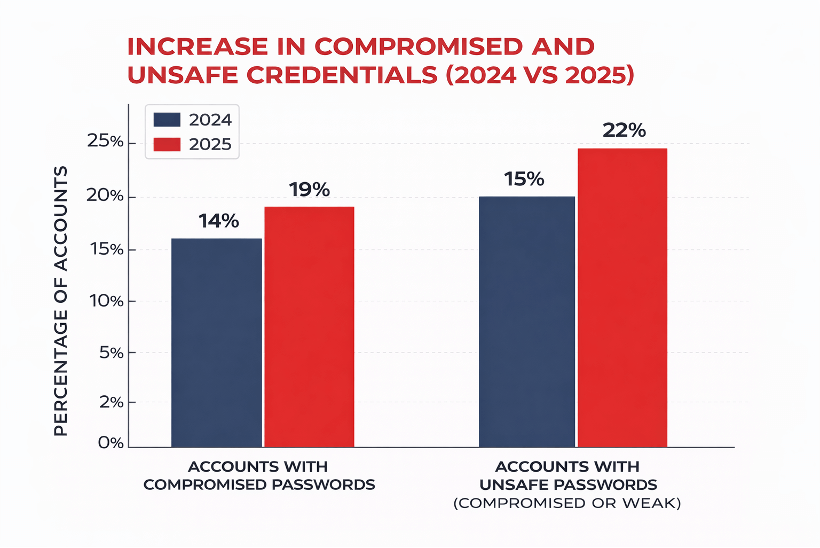
Figure: Chart showing the increase in compromised and unsafe credentials from 2024 to 2025 based on Enzoic’s AD Lite aggregated data. In 2025, a larger portion of accounts had compromised or weak passwords compared to 2024, indicating a growing risk.
As shown above, the prevalence of compromised credentials increased from 2024 to 2025. In 2025, roughly 19% of user accounts scanned by Enzoic’s AD Lite were found to have passwords that had been compromised (exposed in data breaches), up from about 14% in 2024. This uptick of over five percentage points means a greater fraction of users are using passwords that attackers already know. In fact, accounts with unsafe passwords (meaning either compromised or weak) crossed the one-in-five mark in 2025, reaching about 22% of accounts per domain (versus ~15% in 2024).
Compromised passwords are only part of the problem. Many users continue to choose weak, easily guessable passwords, which are highly susceptible to dictionary-based guessing attacks, including offline dictionary attacks if password hashes are ever exposed, and this further adds to the risk of compromised credentials. The AD Lite data shows that the proportion of users with weak passwords (such as “!!!!!!!!” or other common choices) increased significantly from 2024 to 2025. While only about 1.6% of accounts scanned in 2024 used passwords deemed weak, that share jumped to roughly 2.7% in 2025. This is a worrisome increase in poor password hygiene. Even though a weak password hasn’t been leaked in a breach yet, an attacker can guess or crack it with minimal effort. Or, if the hash becomes leaked in a breach, it will be easier to recover the original password.
By combining the figures for compromised and weak passwords, we see that over 22% of all accounts in 2025 had unsafe credentials (either already compromised, or so weak that they’re effectively insecure).
This means more than one in five users had a password that put their account at high risk.
The growth in unsafe-password incidence from 2024 to 2025 indicates that organizations are facing an increasing threat. In short, not only are breached passwords more common, but users’ propensity to set weak passwords has also increased, which creates a larger attack surface. The risk of compromised credentials is amplified when users rely on passwords that attackers can easily obtain or guess.
This mirrors what Verizon sees across real-world incidents: the 2025 Verizon DBIR found that attackers using stolen/compromised credentials is the top initial access vector in breaches. This industry context helps explain why credential abuse continues to show up as one of the most common ways attackers get in, and why reducing unsafe passwords directly reduces breach likelihood.
The upward trend in compromised credentials and related weaknesses is a clear call to action for IT security teams. Fortunately, the same data that highlights these risks can also inform solutions. Enzoic’s AD Lite scan provides valuable visibility into where your Active Directory stands by helping you see your current level of risk and identify exposed or weak passwords. But for a long-term fix, organizations need more than periodic snapshots. That’s where Enzoic for Active Directory comes in, which delivers continuous monitoring, ongoing visibility, and set-and-forget protection that keeps your environment secured as conditions change.
To mitigate the risk of compromised credentials, consider the following steps:
The data from Enzoic’s AD Lite tool makes it evident that the risk of compromised credentials is increasing and cannot be ignored. More broadly, it reinforces a key point: scanning and fixing passwords once is not enough. Because new breaches and exposures happen continuously, truly proactive protection demands ongoing monitoring and repeated remediation to keep the risk of compromised credentials from creeping back up over time. From 2024 to 2025, organizations saw higher proportions of their user accounts flagged for compromised or unsafe passwords, driven by factors like weak password choices, reuse of credentials, and poor account hygiene. The silver lining is that with awareness comes the ability to act. By heeding these insights (tightening password policies, cleaning up old accounts, and continuously monitoring for credential exposure), organizations can reduce their risk. The fight against compromised credentials is an ongoing effort, but it’s one that IT teams can get ahead of by using the right tools (such as Enzoic for Active Directory) and best practices to keep their users and data safe.
AUTHOR
 Josh Parsons
Josh Parsons
Josh is the Product Manager at Enzoic, where he leads the development and execution of strategies to bring innovative threat intelligence solutions to market. Outside of work, he can be found at the nearest bookstore or exploring the city’s local coffee scene.
Run a free Enzoic AD Lite scan to identify compromised and unsafe credentials in your environment