How Attacks Work and How to Stop Them
Credential stuffing is the automated use of collected usernames and passwords to gain fraudulent access to user accounts. It’s a cybercrime technique where attackers use automated scripts to try each credential against a target website. It is considered a subset of brute-force attacks.
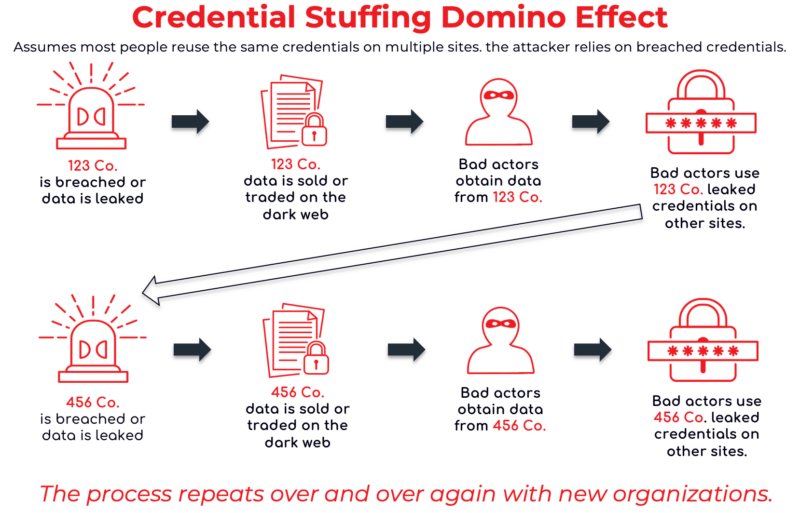
The reason this works is the majority of users reuse the same credentials on multiple accounts. This unfortunate reality means one data breach can threaten many organizations.
There are a lot of headlines around data breaches and how billions of user credentials have been exposed publicly over the last few years. The natural question that comes up is:
“What do cybercriminals do with these stolen credentials?”
Apart from using them to attempt logins to the breached website itself, the second most common thing cybercriminals will do with stolen credentials is use them in an attack called credential stuffing.
Credential stuffing is a volume-based attack that lets an attacker gain unauthorized access to an account. Once inside, they may do all sorts of things — one of which could be accessing all users’ data. If that occurs and the data includes credentials, you could say there was a credential spill. A credential spill occurs when exposed usernames and passwords from one system are released (whether accidentally or deliberately) and then circulate publicly or within criminal communities — and a spill like this often fuels credential stuffing across other sites where users have reused those credentials.
Credential stuffing is a fairly straightforward technique whereby an attacker will use an automated script or application to iterate through their list of stolen credentials, trying each credential against a target web application or list of applications. Whenever a successful login is found, it is recorded for later exploitation.
This attack vector is so effective because 78% of individuals use the same password for more than one account, and 52% use it for at least three accounts. Password reuse is a major cybersecurity risk because it enables attackers to breach multiple accounts with just one set of stolen credentials.
A threat actor compiles or obtains a list of credential pairs (e.g., a username and associated password), typically thousands of entries long, from a third-party site. It “works” because many people will have reused the exact same credential on the target site. They choose a target, often a login form on a particular website, and run a program that attempts to log in with each credential pair.
The Source: Breach Data and Infostealer Logs
Credential stuffing attacks depend on access to real, previously stolen credentials — not random guessing. These credentials come from:
Modern attackers aggregate billions of credentials from these sources, constantly updating their databases as new breaches and infostealer logs appear. The scale and speed of these collections make traditional perimeter defenses ineffective.
Jane has a LinkedIn account. Her account credentials were exposed in the massive LinkedIn breach from a few years back. Unfortunately for Jane, she happens to be one of the users who reuse the same credentials across multiple websites.
After the LinkedIn breach goes public, LinkedIn makes Jane reset her password. However, Jane doesn’t realize that she needs to update her password not just on LinkedIn, but everywhere else she’s using the same login credentials.
Enter Jake. Jake has gained possession of the LinkedIn list of stolen credentials and is a budding cybercriminal. Using an application called Sentry MBA, Jake sets up the LinkedIn list and looks for hits against his favorite shopping site, Amazon.
As it so happens, Jane used the same password for Amazon as she did on LinkedIn and has left her credit card tied to her account. Once Jake has his list of hits, he starts logging into Amazon accounts, looking for ones with home addresses in the same town as him. He happens upon Jane, who fits the bill. The next thing you know, Jake has ordered some pricey items using Jane’s Prime account and lies in wait outside Jane’s house on the day of delivery to snatch the parcels before Jane even knows the order was placed.
This is just one example of a credential stuffing attack and the negative outcomes that can follow. Imagine if, instead of focusing on Amazon, Jake had tried to use those credentials to log into Jane’s employer’s corporate account. The attack could lead to a massive enterprise security breach, exposing sensitive corporate data and business operations to cybercriminals.
Credential stuffing and brute-force attacks are often mentioned together, but they operate very differently. In a brute-force attack, cybercriminals try to guess passwords by testing countless random or patterned combinations until one works. Credential stuffing, by contrast, relies on previously stolen usernames and passwords obtained from data breaches.
Because attackers are using valid credentials, credential stuffing is faster, stealthier, and more effective than brute-force attacks. It also evades many traditional defenses like lock-out policies or CAPTCHA because the login attempts appear legitimate. That’s why protecting against credential stuffing requires continuous monitoring of compromised credentials, not just rate-limiting or password complexity rules.
For a deeper dive into how these two attack types compare — including methods, defenses, and real-world context — read more in Enzoic’s analysis of credential stuffing vs. brute-force attacks.
Cybersecurity research indicates about 1 percent of stuffing attempts are successful. As the number of attempts is in the billions per year, even a 1 percent rate means tens of millions of accounts are taken over annually.
Even a single success can be disastrous — once inside, a threat actor can escalate privileges, move laterally, and deploy ransomware or other malicious payloads.
According to the Verizon Data Breach Investigations Report (DBIR), over 60% of breaches involve credential data, and businesses across every industry experience a median of over 1 million credential stuffing attempts per year.
Given the massive volume of leaked credentials available online, these attacks are now among the most widespread and cost-effective tactics in a cybercriminal’s arsenal.
Credential stuffing attacks are not just a technical nuisance; they create real business consequences. Attackers frequently monetize successful logins through fraud, resale of accounts, or data theft.
It’s estimated that 3–8 percent of attempted logins using compromised credentials succeed, and as much as 90 percent of traffic to enterprise login forms may originate from credential-stuffing bots.
The downstream costs are significant:
Beyond direct losses, these attacks damage brand reputation and weaken confidence in digital systems. The reputational recovery from a credential-based breach can take years — often costing far more than the incident itself.
There are multiple ways to try to detect an attack.
Early detection can help organizations limit damage before widespread compromise occurs.
A primary defense is to ensure the use of unique passwords for each site and confirm that passwords were not previously compromised. Password reuse is what enables credential stuffing, so this practice should be strongly discouraged — both at work and at home. Continue to monitor credentials on an ongoing basis in real time to ensure user login credentials have not been exposed.
Implement strong password policies, enforce MFA where possible, and — most importantly — adopt continuous credential monitoring to identify compromised passwords as soon as they appear in breach data or malware logs.
Enzoic provides enterprise security solutions to protect against credential stuffing attacks and automated login breaches.
Our platform offers:
Enzoic helps protect your website, your company, and your users from credential stuffing attacks by preventing users from using known, compromised credentials.
Was it a breach or credential stuffing, how to tell?
Credential stuffing is a method of active attack by threat actors. A data breach is a result of the exposure of confidential information; this can occur through error, lack of responsibility and security of an organization, or any other different cyberattacks.
Does Single Sign-On (SSO) stop credential stuffing?
SOO reduces the chance that a user’s credentials would be exposed in a breach incident because it reduces the number of “doors”/entry points that an organization needs to make secure. However, it becomes even more integral that the main account used for SSO has a strong, unique, and uncompromised password.
Additional articles: