Enzoic’s proprietary research is powered by a combination of human and automated intelligence to rapidly provide security teams with the most comprehensive protection against credential-based attacks, leveraging actionable, validated threat intel.
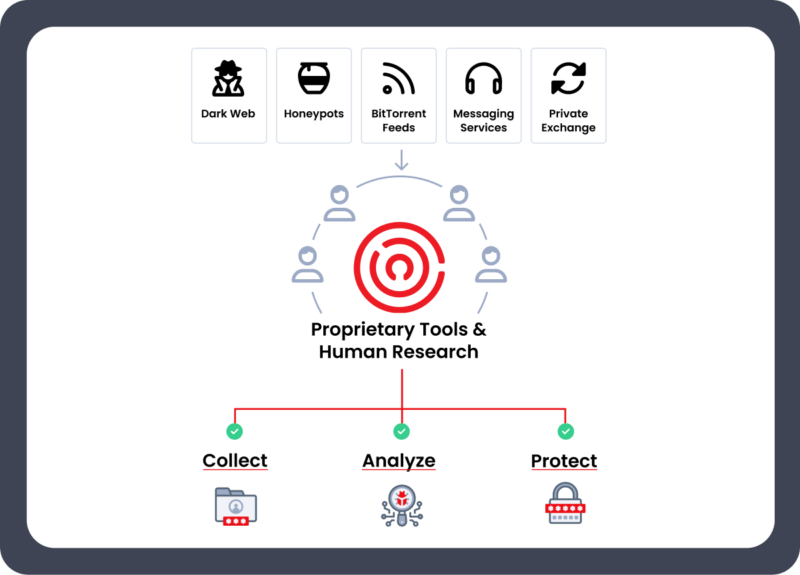
Enzoic uses multiple threat intelligence research techniques. Our trained analysts scour the public Internet, Dark Web, and work with private sources. We’ve also developed proprietary tools that automatically scrape and download, including from short-lived sites often missed by traditional threat intelligence platforms.
In addition, honeypots add credentials not available elsewhere by collecting in real time from actual cyberattacks underway. We also incorporate infostealer data and other malware-harvested exposures when available, strengthening our identity threat intelligence coverage.
Enzoic focuses on threat intel directly tied to user identities and authentication workflows. By monitoring compromised credentials, exposed PII, dark web activity, and malware-stealer data when available, we provide organizations with actionable intelligence that maps to real accounts—not generic indicators.
An identity-first approach gives security and IAM teams the context needed to prevent account takeover and reduce identity-based risk.
While some services rely on clear-text and crackable hashes, Enzoic offers a unique approach that allows comparisons to the original hash.
Because Enzoic can compare against the original hash, organizations can maintain strong, uncrackable hashing standards while still detecting compromised passwords—providing full visibility into credential risk across modern authentication environments.
Although compromised passwords are a major driver of attacks, they represent only part of the identity risk surface. Enzoic’s threat intel includes exposed credentials, PII, payment card data, and other identity attributes that appear in breaches and infostealer logs.
Broader visibility strengthens detection across the full lifecycle of identity threats.
Enzoic’s threat research prioritizes delivering intelligence that security teams can act on immediately. Our data is validated, normalized, and deduplicated to eliminate spam lists, synthetic records, recycled breach dumps, and other low-value noise that can create alert fatigue.
Each exposure we collect is enriched to ensure the threat intel we provide is clean, relevant, and aligned with real credential and identity risks—offering meaningful insight rather than inflated or noisy breach datasets.
Our database contains breaches of all sizes. It goes beyond well-publicized attacks to capture numerous microbreaches that make no headlines but carry outsized risk. These smaller exposures—often sourced from malware logs and lesser-known sites—are essential to identity-centric threat intel and are widely missed by traditional providers.
Enzoic’s threat intelligence also supports broader industry research, including contributions to the Verizon Data Breach Investigations Report (DBIR). Our credential exposure insights help enrich one of the cybersecurity industry’s most trusted annual reports, demonstrating the depth, reliability, and relevance of our threat intelligence.
Enzoic’s proprietary technologies quickly ingest and index new exposures, ensuring security teams have access to the most current threat intelligence available. Our compromised credential and password data is refreshed multiple times each day, providing timely visibility into emerging risks across the threat landscape.
Continuous ingestion ensures real-time detection of credential-based threats.
1,112
80%
72%
10.07
26,000
Make detecting and eliminating compromised passwords in Active Directory easy with a simple plug-in. Start protecting for free.
Try Now