Why Credential Monitoring is Essential When Attackers are Logging in, Not Breaking In
For cyber attackers, stealing a single set of login credentials can be as good as stealing the keys to the kingdom. IBM’s 2025 Cost of a Data Breach Report drives home that point: attackers today are often “logging in rather than hacking in,” reinforcing how frequently they rely on stolen passwords. Because IBM attributes incidents to the attacker’s first move, cases that appear under phishing, third‑party vendor compromise, or other categories often rely on the same underlying issue somewhere in the attack chain: a compromised account. In 2025, phishing jumped to the number one attack vector (16% of breaches), replacing stolen credentials (last year’s top entry method). Yet tellingly, those phishing emails often delivered stealthy infostealer malware to scoop up passwords and other credentials. No matter the entry point, the recurring theme is that a misused username and password often do the heavy lifting for attackers. IBM’s research sets the stage for modern risk management: strengthening credentials. From setting secure passwords to continuous credential monitoring, organizations have options to shrink this risk and prevent stolen logins from turning into full-blown breaches.
Phishing rose to the top largely because adversaries now mass-produce convincing lures with generative AI tools. Yet the goal is seldom the email content itself; it’s the credentials harvested after a user clicks. Modern phish kits are designed to:
Industry sources report that many phishing kit operators do not use the stolen logins themselves. Instead, they act as suppliers in a criminal supply chain. Initial Access Brokers and other threat actors harvest credentials (via phishing kits, infostealer malware, etc.) and then dump these fresh “logs” on dark web marketplaces for sale. Phishers stick to what they do best, collecting credentials, and then sell those credentials on dark‑web forums to more technically skilled adversaries who weaponize the logins for lateral movement, privilege escalation, and data exfiltration.
A strong credential monitoring program disrupts this chain in two ways. First, proactive password screening prevents users from picking passwords that are already known to attackers (found in breach dumps), nullifying easy credential-stuffing attacks. Second, continuous dark-web surveillance detects fresh credential leaks, alerting security teams to reset those accounts before criminals can weaponize them. When phishers find their newly stolen logins go stale within hours after exposing them, their ROI plummets and campaigns lose steam.
Vendor relationships create natural trust tunnels. Attackers exploit this by hijacking a supplier’s credentials, then “walking in” to the primary target’s environment as a legitimate partner. IBM records that these third-party and supply-chain compromises accounted for ~15% of breaches and took the longest to detect (nearly nine months on average). Malicious activity is hard to spot because it masquerades as routine partner traffic for months.
Supply‑chain breaches often begin with stolen identities. The quickest, most cost‑effective way to reduce this risk for your partners is to identify any exposed credentials belonging to your organization and disable them before an attacker can use. To further protect your own environment, assess existing and prospective vendors to confirm they monitor their users for credential compromise and, where you have legitimate access, proactively test the credentials of partners, contractors, and other third‑ and nth‑party users for signs of compromise. NIST guidance recommends checking for compromised credentials, and this is increasingly regarded as essential.
The result is a hardened supply-chain mesh where exposed credentials, even those held outside your direct perimeter, cannot quietly enable a foothold for attackers.
The direct use of stolen or reused passwords still drives roughly one in ten breaches according to the latest report and remains among the slowest breach types to discover. Attackers love this path because valid logins bypass many preventive controls, the traffic looks normal (delaying alarms), and password reuse means one breach often unlocks multiple services. IBM’s data shows that breaches initiated with stolen credentials have a mean time to identify and contain of about 246 days. That’s eight months of undetected, “invisible” access for the intruder.
Continuous credential monitoring flips that script. By detecting stolen credentials in real time (whether via public breach databases, paste sites, or malware logs) and binding those alerts to automated password resets or login challenges, organizations can shrink attacker dwell time from months to hours. Fewer valid credentials available to criminals means fewer silent footholds and far less cleanup expense.
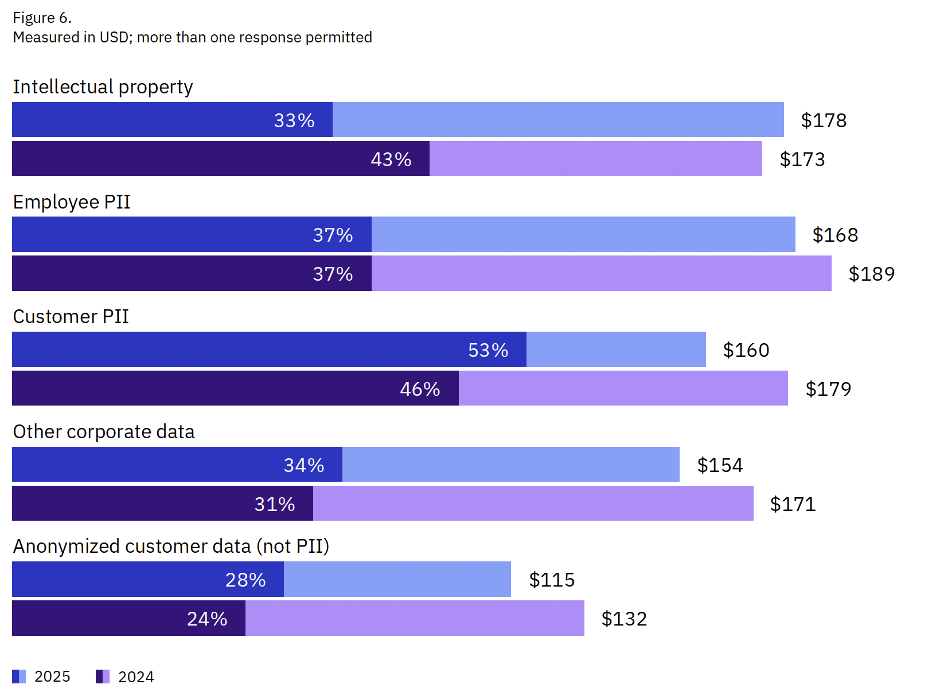
In 2025, customer PII was the most commonly compromised data type
IBM shows a yawning cost gap between organizations that heavily automate security and those that rely on manual efforts, nearly $1.9 million less per breach on average for the former. Identity protection is no exception. Large enterprises might manage hundreds of thousands of passwords; manually checking each against ever-growing breach dumps is impossible.
Modern credential monitoring platforms employ and automation to:
This machine-speed response is the only practical way to outpace attackers who also automate their credential-stealing pipelines.
“Today, many attackers are logging in rather than hacking in. To combat this issue, it’s critical to prevent attackers from obtaining those credentials in the first place.”
— IBM, 2025 Cost of a Data Breach Report
Phishing may sit at the top of IBM’s charts, yet once methodological nuances are set aside the 2025 report delivers a familiar lesson: attackers win when they hold valid credentials. By making continuous, automated credential monitoring a core element of security programs for employees, contractors, and vendors alike, organizations can sever that lifeline and force adversaries to rely on louder, riskier tactics. With breach costs stubbornly high and identity‑based threats evolving every day, vigilant monitoring for compromised credentials is the most cost‑effective way to keep the next headline breach off the balance sheet.
AUTHOR
 Josh Parsons
Josh Parsons
Josh is the Product Manager at Enzoic, where he leads the development and execution of strategies to bring innovative threat intelligence solutions to market. Outside of work, he can be found at the nearest bookstore or exploring the city’s local coffee scene.