Now in its eighteenth year running, the Verizon Data Breach Investigations Report (Verizon 2025 DBIR) continues to occupy its usual place at the forefront of cybersecurity research analysis and reporting. Covering a record 22,052 security incidents in this year’s installment, it provides an unparalleled view of the cybersecurity climate that many researchers, security professionals, and businesses rely on to drive decision-making and cybersecurity practices in the face of a dynamic and often opaque threat environment. This year, Enzoic is proud to be an official contributor to the report, having provided data and analysis regarding the effects of infostealer malware on the compromised credential ecosystem.
A quick note: all following in-text citations and graphics/figures are from the 2025 DBIR unless otherwise noted.
The very first report summary figure (DBIR pg 10, and included below) once again confirms what has sadly been the case for years now, that credentials are still the top initial access vector overall. It’s not totally bleak though: the number of incidents involving credentials did decline slightly year-on-year…perhaps the message is finally getting through, and organizations are adopting meaningful credential security practices? (Maybe? Please? As a company whose mission is improving credential security, we really hope so). Unfortunately, while credential attacks decreased slightly, the exploitation of vulnerabilities for initial access saw a whopping 34% increase, partly due to the exploitation of edge device or VPN software vulnerabilities (Edge devices serve as entry points to networks– routers or internet gateways for example). This is a critical finding that should serve as a call to action for organizations of all sizes to secure these devices. Indeed, this first chart from the report essentially lays out three pillars for a strong cybersecurity posture: secure your credentials, patch/update your devices, and educate your employees/users.
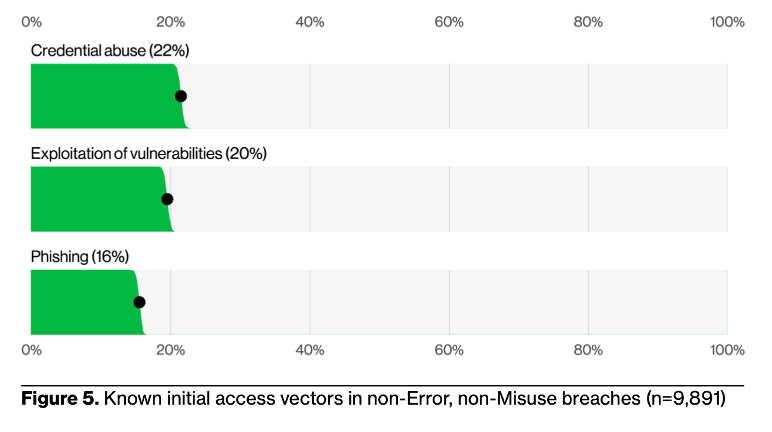
At Enzoic, our research primarily concerns the role of compromised credentials in the threat landscape, so we often look to the DBIR to help us understand the big picture and avoid the pitfalls of myopia, ensuring our work and products continue to provide value and defend against cyberthreats. This section will cover the main ways that threat actors are using compromised credentials as discussed in the DBIR.
As we touched on previously, credentials are the favorite initial access vector of cybercriminals. An initial access vector is the first opportunity that threat actors exploit in perpetrating a cybercrime. In the oft-used home-burglary analogy this could be picking a lock or breaking a window. Credentials are often likened to keys, and one can imagine how simple breaking into a house would be if you already have the keys– no wonder they remain threat actors’ top choice. But computers aren’t houses, so let’s look at how this actually happens.
Credentials as an access vector make their biggest showing in the Basic Web Application Attack (BWAA) pattern, as one might expect. Nearly every web application (email, social media, games, banking, Netflix) requires authentication, and has a publicly accessible login page, which is the main target in this type of attack. Sometimes threat actors may have a verified credential for a specific purpose1– this is referred to as the “Use of stolen creds” – or they may use automated scripts or bot networks to guess thousands of credentials until they find a valid one– this is known as “brute forcing”. DBIR Figure 56 below shows how frequently these two are used; it’s also worth noting these categories are not exclusive: a threat actor might use a stolen credential to login, and then a backdoor vulnerability to move deeper into the application. BWAAs can be the ends in themselves in the case of account take-over (ATO), an enormous source of fraud and revenue loss, but also can play a significant role in the more complex System Intrusion attack pattern, which includes incidents involving the deployment of malware and data theft (more on that later).
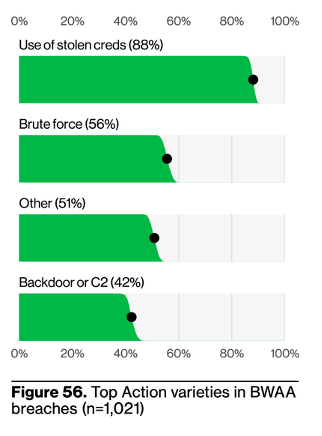
It would be hard to talk about BWAAs from 2024 without discussing the data breaches affecting Snowflake customers early in the year. While Snowflake (a cloud data storage company) itself didn’t get hacked, so many of its customers’ accounts did that the series of events has taken on their name. Regardless of where the blame lies, subsequent research has shown that “approximately 80% of the accounts leveraged by the threat actor in this attack had prior credential exposure” (DBIR pg 16). Indeed, our research at Enzoic showed how easy it was to quickly download, find, and compile hundreds of stolen Snowflake credentials along with the exact customer endpoints for which they were valid.
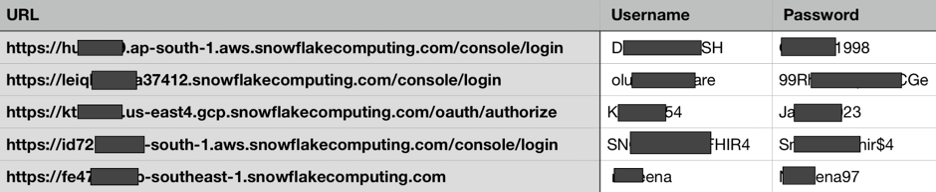
Examples of Snowflake customer account credentials found in infostealer data traded by threat actors. Source: Enzoic
At Enzoic, we process large amounts of data from infostealers, but we’re typically focused on credential extraction and rapidly delivering this data to our customers, so we were excited to see an in-depth analysis of infostealer logs in this year’s DBIR. One of the most fascinating/highly concerning findings was the rate of infections of enterprise devices. While it makes some sense that people often download and open sketchy software on their personal computers (gotta get that new free Fortnite skin…who cares where it comes from), evidence suggests 30% of the analyzed infections were on enterprise devices (DBIR pg 56). Yikes. Password reuse and BYOD policies make infostealers a huge risk for organizations as it is, and if CISOs weren’t taking this seriously yet, then time is of the essence.
Another fascinating (and highly concerning) finding was the co-occurence of ransomware victimization and appearance of domains in infostealer logs. The report states “By examining some of the victims posted to the ransomware extortion sites, we found that 54% of the victims had their domains show up in at least one infostealer log or in marketplace postings, and 40% of those logs contained corporate email addresses.” Let’s take a closer look at the accompanying chart:
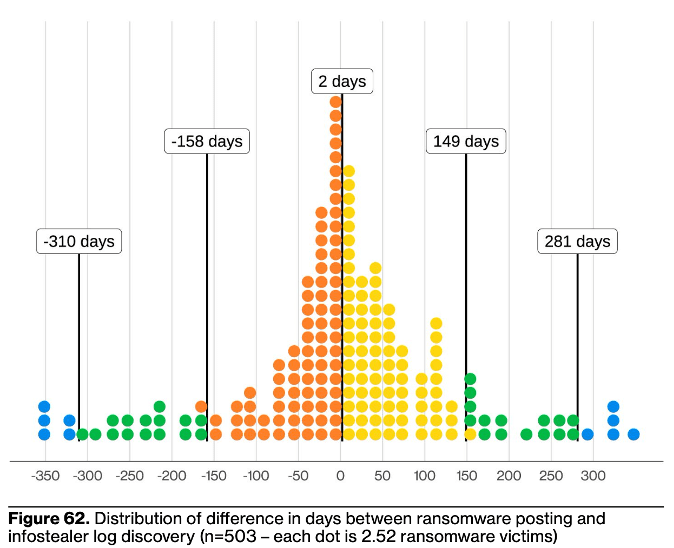
This is extremely intriguing. We can see the largest spike is just prior to 2 days, i.e. many ransomware attacks are disclosed just a day or two after a victim’s credentials appear in an infostealer log. Of course, we must be wary of the old post-hoc-ergo-propter-hoc fallacy, but as the DBIR team says, and this threat researcher agrees, “it does seem to corroborate the anecdotal evidence that leveraging stolen credentials from infostealers is a key tactic used by some ransomware operators” (DBIR pg 57). This certainly begs for more research to be done, but does also align with common sense. We know that credentials are an increasingly favored initial access vector in Ransomware deployment (see Figure 45 below), and these infostealer logs are one of the freshest and most available credential access sources in today’s threat environment.
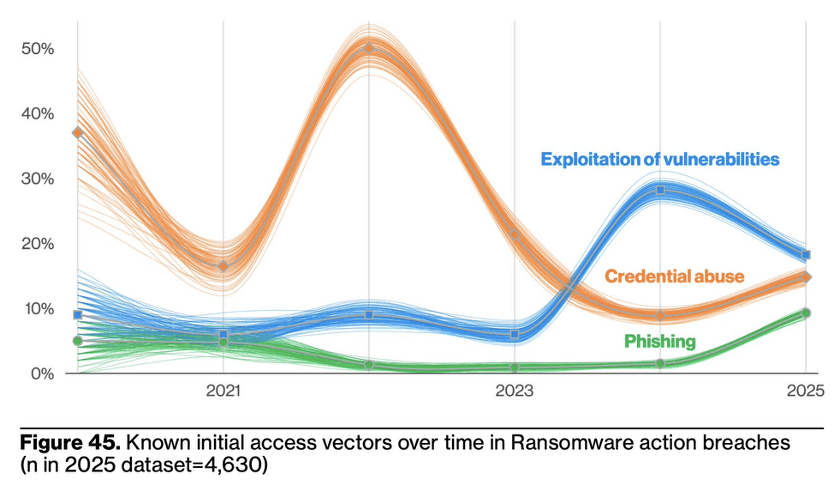
Though we at Enzoic don’t typically deal with ransomware directly, it’s still a huge concern for us in the landscape at large due to the impact it has on organizations and users worldwide. The disruptions to services and financial losses (or gains, if you’re a cybercriminal) are staggering.
“When discussing Ransomware, it is important to note that it really captures the monetization of system access, and that around 42% of breaches involve compromised credentials, an exploited vulnerability or the use of phishing.” – DBIR pg 40
This year, Ransomware “accounts for 75% of breaches in [the System Intrusion] attack pattern” (DBIR pg 40), and the figure below shows how System Intrusion has not only increased significantly, but taken the lead over Denial of Service.
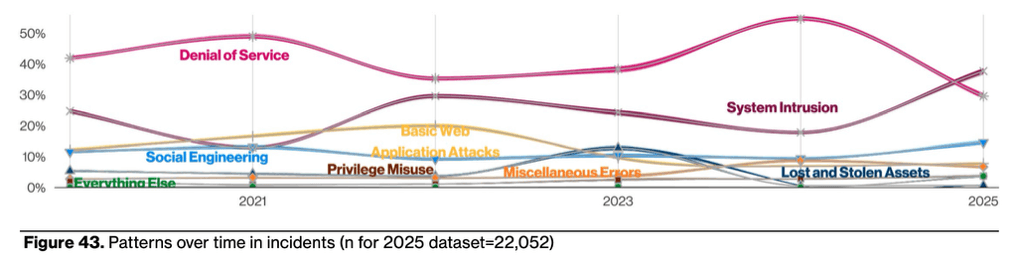
A quick aside: we’ve posted a couple times already this year about the impact of ransomware on the healthcare industry during 2024; this was further borne out in the DBIR data. Rates of compromised Medical data more than doubled since last year’s report, and is likely due to ransomware: “As the Healthcare sector gets more and more attention from ransomware operators, we see this percentage increase.” (DBIR pg 34). Yikes.
Public and organizational attitudes about multi-factor authentication (MFA) seem to range from ‘a useless pain in the neck’2 to ‘once it’s enabled, we need never worry about security again.’ Neither of these are particularly accurate or helpful from a security posture standpoint unfortunately, and it seems like some better education might help folks’ awareness and security decisions. MFA bypass is one of those things that seems like it could never happen to you (much like identity theft in general); perhaps it would behoove everyone to take a look at pages 47 and 50 of the DBIR to understand why this is probably not a wise assumption. Threats and techniques are constantly shifting, and “a dedicated adversary will do whatever works.” (pg 47). Let’s include the chart of Microsoft 365 MFA bypass attacks– a specific breakdown like this can be helpful in making these vulnerabilities less abstract:
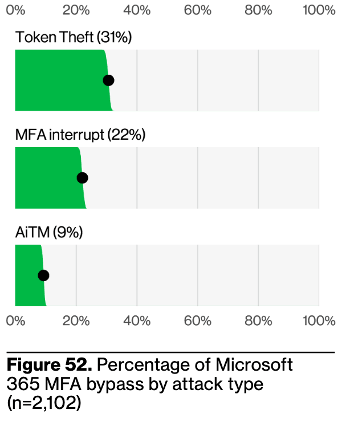
Page 50 is a deeper discussion of SIM swapping, which is particularly interesting given the DBIR team being part of Verizon, one of the largest cell phone providers in the US. There’s a great suggestion at the end of this section– “providing some more authentication friction to customers who have recently changed their devices might not be such a bad idea for critical services that are frequently targeted by fraud.” This should serve as a more general reminder that authentication friction can be controlled and used in different degrees. While more friction is more secure, the most effective security practices are the ones that actually get used, and it’s important to recognize the realities that many organizations face in terms of user friction. Rather than advocating for enormous passwords and constant MFA, we need to present more options and support their adoption. Using signals (e.g. a recent device change) to temporarily require a second factor is a great strategy to mitigate risk if always-on MFA is not an option. This is also another use-case for compromised credential intelligence: while we certainly recommend that any compromised password is immediately changed, credential compromised alerting can also be used as signal intelligence for engaging a second factor, or in concert with other detection systems to alert on activity that may otherwise not constitute sufficient risk on its own.
“…having [MFA] enabled should not make your detection and monitoring processes complacent.” DBIR pg 47
It is always a challenge to summarize the DBIR, because the authors are clear, concise, and don’t waste any space (or readers’ time). That said, we understand that not everyone is a cybersecurity researcher with several days to dedicate to reading and data analysis (it’s okay to be jealous), and may benefit from an abridged version, or reading only the sections that apply most to their own situation. As such, we’ve only really touched on the points that concern credential or authentication security so far, but we want to mention some of the other sections for further reading if they apply to you.
The Industry Breakdowns: If you’re a security professional or decision-maker for an organization, looking at your organization’s specific industry breakdown is a great way to get a handle on the most relevant threats to your data security.
Focused Analyses: These look at data breaches by organization size or type, including small-or-medium businesses (SMBs), large businesses, and public sector (including Federal and State, Local, Territorial, and Tribal). This is a special section for this year, and really worth a review of the section most relevant to your organization, as some threats are outsized for certain groups; particularly concerning is how badly malware and ransomware affect SMBs.
Regional Analyses: As you’ve probably guessed, these slice up the security incidents by region, specifically across 5 global divisions. This one is probably most useful for cybersecurity professionals who want to understand the global threat landscape.
Last year we talked about financial motives reigning supreme for threat actors around the world, and that certainly still seems to be the case, but we should note the increase of Espionage as a threat actor motive.
We also saw significant growth in Espionage-motivated breaches in our analysis, which are now at 17%. – DBIR pg 11
As is pointed out in the report, espionage and financial motivation are not mutually exclusive, and may be a convenient way for state-sponsored threat actors to multitask. With increasing global political instability and multiple dynamic conflicts raging, it’s no time to let the defenses down. We certainly see a lot of politically-motivated rhetoric on threat actor communication platforms, including bundles of credentials on offer that are tailored to attack a particular region or group.
Enzoic remains dedicated to helping organizations achieve strong credential security, especially as current data highlights that many businesses continue to face breaches and costly consequences for falling short of this goal. The point is not to victim-blame here though: it’s truly unfortunate that we have to spend so much time and resources contending with cadres of petty criminals, organized cybercrime, state-sponsored scammers, and the like. We can all do more to keep each other, and our data, safe however, and the message remains the same as previous years: users need to improve password hygiene (comply with established best-practice frameworks, such as NIST’s current password recommendations) and stay vigilant against phishing and fraud). It is also incumbent upon organizations, as custodians of our data, to take these threats seriously, and incorporate credential monitoring, MFA, vulnerability remediation, and employee/user education against scamming and phishing. Nobody likes shouldering the cost (in time and money) of cybersecurity, but this persistent and pervasive abdication of prevention and defense means that all of us shoulder the cost whether we want to or not: the costs of data breaches come to us in increased prices, increased insurance premiums, increased credit-card fees, etc, even if we escape the direct effects. It is all unnecessary risk and expense, and we should consider each DBIR a call to collective action to protect ourselves, each other, and reduce the opportunities for cybercriminals to profit from their cybercrime.
2Other parts of the human body have also been mentioned in this context.
AUTHOR
 Dylan Hudson
Dylan Hudson
Dylan leads the Threat Research team at Enzoic, developing and implementing cutting-edge threat intelligence infrastructure to help protect users and organizations from cyberattacks. When not at work, he can be found hiking and biking in the Rocky Mountains or playing traditional Celtic music on various stringed instruments.
Stop Compromised Credentials and start exploring for free – up to 20 users or 2000 API calls.