The 2023 data from Enzoic for Active Directory Lite (also known as Enzoic for AD Lite Password Auditor) offers a revealing glimpse into the current state of cybersecurity, highlighting a significant increase in risk factors that lead to data breaches. This article seeks to provide a benchmark based on Enzoic’s audit of nearly 6000 corporate domains, with data derived from a large sample of Active Directory environments where users’ credentials were securely scanned using Enzoic for Active Directory Lite. The free password auditor has been at the forefront of monitoring and analyzing user data to identify vulnerabilities and trends within environments that can inform better security practices. In 2023, our data revealed insights that are crucial for understanding common risk factors organizations are currently seeing.
Enzoic for AD Lite Password Auditor is an innovative, cost-free tool designed to seamlessly integrate with an organization’s Active Directory environment. This tool provides invaluable insights into various aspects of user account security, helping organizations to identify and address potential vulnerabilities effectively.
The analysis of 2023 data from over 8 million user accounts scanned by Enzoic reveals a concerning pattern: nearly 15% (1.2MM) of accounts were found to be using unsafe passwords (compromised or weak passwords). This finding is a reminder of the ongoing battle against data breaches and the need for organizations to continually monitor passwords in their environment for compromise as recommended by NIST. This significant figure stresses the prevalence of compromised passwords as a leading cause of data breaches, as reported by industry giants Verizon and IBM.

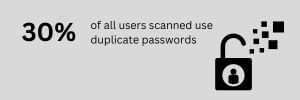
One notable trend is the persistent increase in users with duplicate passwords, at nearly 30% of all users scanned. This may be attributed to administrative oversight, such as setting a default password without enforcing a change. Such practices can create significant security gaps, increasing the chances of account compromise and lateral movement in an environment.
Another concerning observation is that roughly 10% of users scanned in 2023 had expired passwords. This points to a gap in enforcing or following existing organizational policies. It’s a clear indication that despite having policies in place, their implementation and adherence remain a challenge.
In 2023, we introduced the tracking of stale accounts and uncovered over 1.1 million such accounts. These inactive but potentially exploitable user accounts increase an organization’s attack surface. They represent a hidden danger, as they can be accessed by former employees and lack user interaction for password changes in response to compromise or policy updates. This aligns with Microsoft’s data which states that over 10% of Active Directory accounts are stale.
Alarmingly, the average number of users without passwords per domain surged from virtually none in previous years to thirteen in 2023. This represents an open invitation to unauthorized access, highlighting a critical area of vulnerability that needs immediate attention.
Overall, there has been a consistent rise in the number of users with compromised or weak passwords, reaching an average of 199 per domain in 2023 compared to 192 per domain in 2022. This increase underscores the need for stronger password policies and more stringent security practices. Measures like prohibiting the use of passwords that are compromised or commonly found in cracking dictionaries are essential steps in mitigating this risk.
Interestingly, the trends in compromised and unsafe passwords mirror broader industry patterns. The cybersecurity talent shortage, particularly evident in the ‘Great Resignation‘ among CISOs may be contributing to these lapses in security. This suggests that the shortage of skilled cybersecurity professionals is leaving organizations exposed to risks, leading to outdated policies and unaddressed stale accounts. Therefore, it is crucial for smaller security teams to employ tools that can efficiently pinpoint weaknesses in their systems.
Strengthen your defenses with Enzoic for AD Lite Password Auditor. It is a critical tool in highlighting an organization’s risk level. The findings reveal a worrying rise in account-related risks and weak security practices, translating these risks from mere statistics to tangible threats across various organizational sectors. The increase in duplicate passwords and the alarming number of accounts without any password security, combined with over a million stale accounts, underscore the need for stronger cybersecurity measures across all industries. These issues, exacerbated by broader challenges like the cybersecurity talent shortage, demonstrate the necessity for tools like this to help organizations easily identify gaps in their environment. Its capabilities in identifying compromised, weak, and shared passwords, along with accounts that have security oversights, make it an indispensable part of any cybersecurity tool stack.
Enzoic’s free tool simplifies password auditing for AD admins. In addition to identifying weak passwords, it detects compromised passwords on the Dark Web or those shared by multiple users.
The reports also provide insights into accounts with empty passwords, administrative permissions, and non-expiring passwords. Additionally, admins can access a summary of inactive accounts, streamlining Active Directory.
Download Enzoic for Active Directory Lite today to immediately gain crucial insights into your environment’s security status against vital risk factors.
Q: Why is the 2023 data on Active Directory compromised password detection significant?
A: The 2023 data provides new insights into cybersecurity risks, especially the increased prevalence of compromised passwords. It shows the importance of proactive password management and the effectiveness of detection tools in protecting corporate domains.
Q: How can Enzoic for Active Directory Lite help with Active Directory compromised password detection?
A: Enzoic for AD Lite helps by scanning and comparing user credentials against a comprehensive database of known compromised passwords. This proactive approach is vital for mitigating risks associated with third-party data breaches and maintaining robust security standards.
Q: What are the benefits of using a tool like Enzoic for AD Lite?
A: Enzoic for AD Lite provides several benefits, including the prevention of data breaches, enhancement of security postures, and partial compliance with industry standards such as NIST. They are a crucial component in keeping your environment secure. For more complete compliance with a host of security standards and automated remediation, consider looking at the full solution.
Q: How does Active Directory compromised password detection align with modern cybersecurity practices?
A: Modern cybersecurity practices emphasize the importance of early detection and response. Compromised password detection aligns with this by identifying vulnerabilities before they can be exploited, thereby strengthening an organization’s overall security stance.
AUTHOR
 Josh Parsons
Josh Parsons
Josh is the Product Marketing Manager at Enzoic, where he leads the development and execution of strategies to bring innovative threat intelligence solutions to market. Outside of work, he can be found at the nearest bookstore or exploring the city’s local coffee scene.
Easy-to-install plugin that gives you a frictionless way to identify, monitor, and remediate unsafe passwords.